Computerized systems are integral to pharmaceutical manufacturing and quality operations. Compliance has long relied on Computer System Validation (CSV), a structured method that documents and verifies that systems consistently perform as intended. Although effective, CSV has evolved into a process that is dominated by documentation, often at the expense of system performance and product quality.
The FDA first introduced the concept of Computer Software Assurance (CSA) in its 2022 draft guidance. On September 24, 2025, the agency finalized this guidance, establishing CSA as the modern, risk-based framework that builds on CSV while emphasizing critical thinking, efficient testing, and patient safety as the primary focus.
This article examines the principles of CSV and CSA, compares their differences, and highlights how the transition from CSV to CSA streamlines validation while maintaining regulatory expectations.
– Advertisement –
What is Computer System Validation (CSV)?
Computer System Validation (CSV) is the documented process of ensuring that a computerized system performs consistently and reliably in line with its intended use and regulatory requirements.
In the context of Good Manufacturing Practice (GMP), CSV is required for any system that directly or indirectly impacts product quality, patient safety, or data integrity. Regulatory authorities, including the FDA, EMA, and WHO, have long regarded CSV as a cornerstone of compliance, as it is directly linked to 21 CFR Part 11 and EU GMP Annex 11 requirements for electronic systems and records.
The principle behind CSV is that systems must not only be technically sound but also demonstrably controlled. This requires evidence that they are implemented in accordance with predefined specifications, that they function as intended under all expected operating conditions, and that they remain validated throughout their lifecycle.
| Phase | Deliverable | Purpose | Example in Pharma |
|---|---|---|---|
| URS | User Requirement Specification | Captures business/user needs | LIMS must store audit trail |
| FS/DS | Functional/Design Specs | Technical translation of URS | Secure log-in logic |
| IQ | Installation Qualification | Ensures correct installation | Server & DB setup |
| OQ | Operational Qualification | Confirms functions work | Report generation test |
| PQ | Performance Qualification | Validates real-world use | Batch release workflow |
Scope of Application
CSV applies to a broad spectrum of computerized systems used in the pharmaceutical industry. Examples include:
- Manufacturing Execution Systems (MES): Controlling and monitoring shop-floor activities, including equipment operation and batch traceability.
- Laboratory Information Management Systems (LIMS): Managing analytical results, sample tracking, and release decisions.
- Electronic Batch Records (EBR): Capturing production data in place of paper-based documentation.
- Electronic Quality Management Systems (eQMS): Managing deviations, CAPAs, complaints, and change control.
- Spreadsheets and Custom Tools: Even simple Excel spreadsheets that process GMP-relevant data fall within the scope of CSV.
Any system that generates, processes, stores, or transmits GMP-critical data must undergo validation.
The CSV Lifecycle Approach
The traditional CSV approach follows the V-Model, a framework where each stage of system development has a corresponding verification activity.
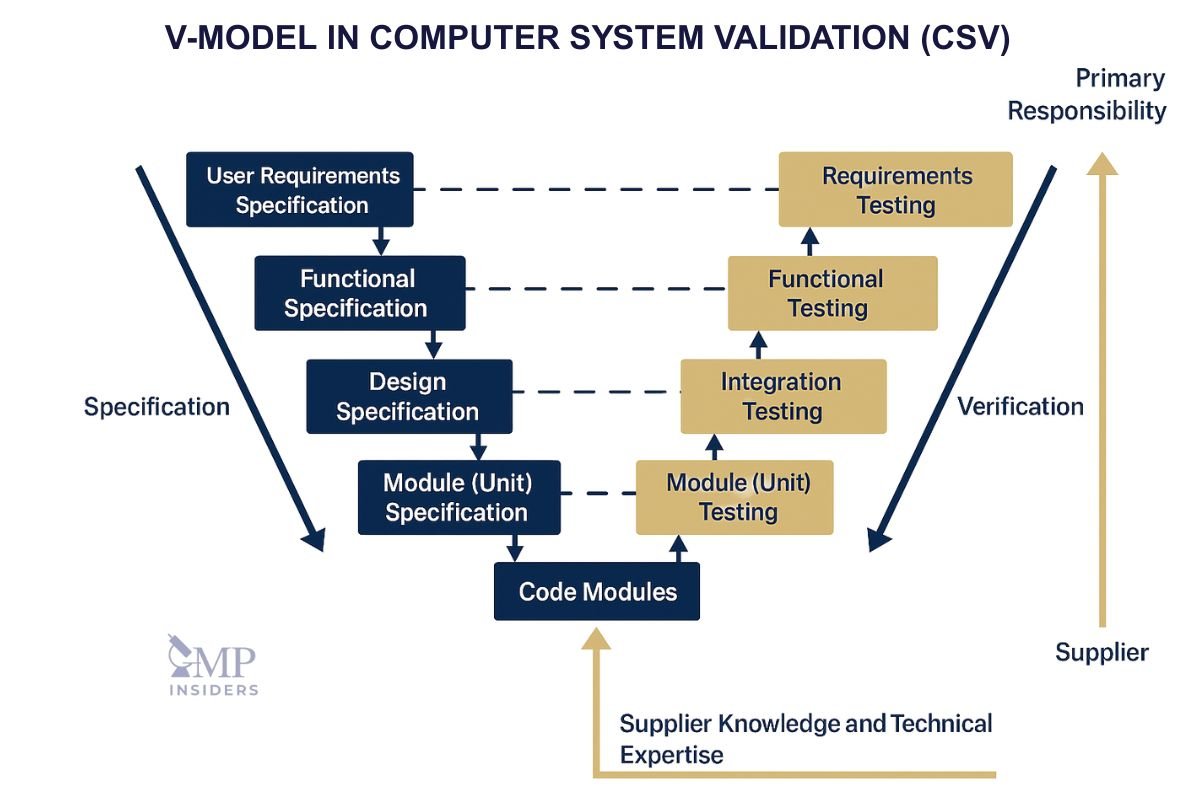
- User Requirement Specification (URS): Defines what the system must achieve, written from the business and user perspective.
- Functional Specification (FS) and Design Specification (DS): Translate the URS into technical descriptions of how the system will achieve the defined functions.
- Installation Qualification (IQ): Verifies that the system hardware and software are correctly installed and configured according to vendor specifications.
- Operational Qualification (OQ): Confirms that functions operate as intended across defined ranges and conditions. OQ typically involves executing detailed test scripts covering each function in scope.
- Performance Qualification (PQ): Demonstrates that the system performs reliably in the actual user environment.
The lifecycle also requires Change Control, Periodic Review, and Decommissioning Procedures to maintain validated status throughout system use.
Common Challenges and Limitations
Although CSV has provided a structured framework for decades, its limitations often become clear in practice. Many of these challenges are interconnected, reinforcing inefficiencies and making it difficult to strike the right balance between compliance and true system assurance.
- Overemphasis on Documentation
CSV frequently prioritizes paperwork over system performance. This can result in:
- Hundreds of scripted test cases for low-risk functions
- Time and effort diverted away from validating critical features that directly affect patient safety
- Resources and Time Intensity
The heavy documentation workload often translates into delays. For example:
- Validation projects extending implementation timelines
- Laboratories waiting months for a new LIMS to go live because resources are tied up in document preparation, review, and approval
- Difficulty Aligning with Agile Development
Agile methodologies emphasize frequent releases and incremental improvements, but CSV’s rigid approach struggles to adapt:
- Linear lifecycle incompatible with rapid updates
- Excessive revalidation or compliance gaps when agile cycles outpace validation efforts
- Inconsistent Risk Prioritization
Another challenge lies in how CSV distributes validation effort evenly across all system functions, regardless of impact:
- Trivial tasks (e.g., formatting a report) receive the same attention as critical operations (e.g., calculating sterile batch yields)
- Resources are wasted on low-value activities instead of focusing on patient-safety-critical processes
- Audit-Centric Approach
Finally, CSV has historically been shaped by a culture of inspection, where the volume of documents measured success. This results in:
- Companies emphasizing “audit readiness” over actual system assurance
- A persistent disconnect between compliance activities and real system reliability
What is Computer Software Assurance (CSA)?
Computer Software Assurance (CSA) is the FDA’s modernized framework for validating computerized systems. Unlike CSV, which places heavy emphasis on generating documentation, CSA focuses on risk-based assurance. Its central principle is that validation effort should be proportional to the impact of the system function on patient safety, product quality, and data integrity.
The FDA’s intent with CSA is not to relax compliance requirements but to shift industry practices away from documentation as a proxy for assurance, and toward critical thinking, science-based testing, and efficient resource allocation.
Scope of CSA
CSA applies to non-product software used in manufacturing and quality systems that is regulated under 21 CFR Part 11 and Part 820. Similar to CSV, examples include:
- Electronic Quality Management Systems (eQMS): Deviations, CAPA, complaints.
- Manufacturing Execution Systems (MES): Batch management, equipment tracking.
- Laboratory Systems: LIMS, CDS (Chromatography Data Systems), environmental monitoring tools.
- Supplier and Training Systems: Vendor qualification, training records.
Key Principles of CSA
CSA is built on principles that shift validation away from rigid, document-heavy practices and toward a smarter, risk-driven strategy. These principles emphasize efficiency, critical thinking, and alignment with modern software lifecycles.
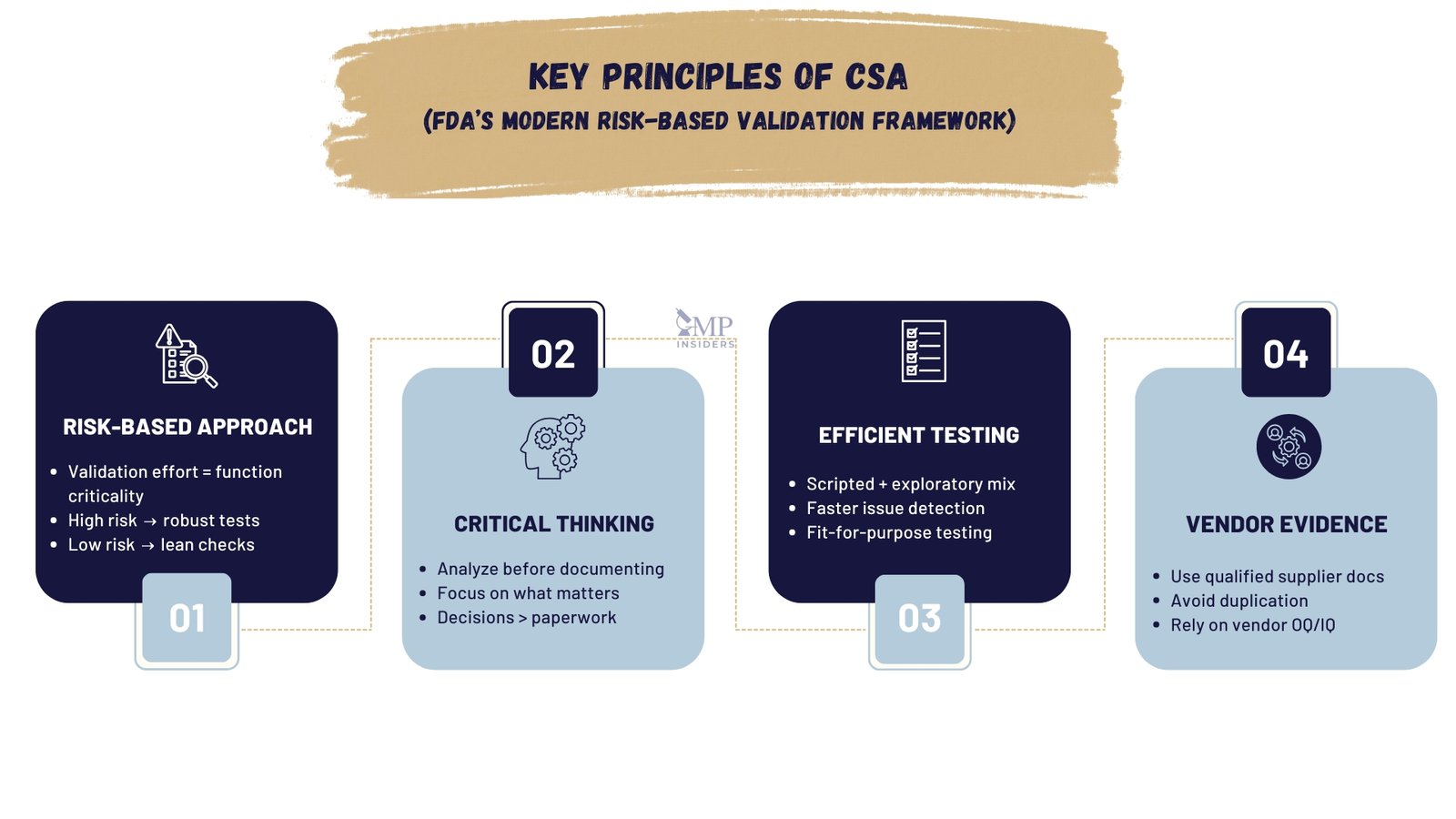
- Risk-Based Approach
The level of validation effort is based on the risk that a system function poses to patient safety and product quality.
- High-risk functions (e.g., calculation of critical process parameters, automated batch release decisions) require robust, documented testing.
- Low-risk functions (e.g., formatting of non-critical reports, administrative settings) may require minimal assurance activities.
- Critical Thinking Before Documentation
Instead of treating documentation as the goal, CSA promotes critical analysis to determine:
- What functions are most critical to control?
- What risks are associated with failure?
- What level of testing provides adequate assurance?
- Testing Efficiency
CSA encourages the use of unscripted and exploratory testing where appropriate, particularly for low-risk functions. This approach allows testers to identify issues more effectively than rigid pre-written scripts.
- Leveraging Vendor Documentation
Rather than duplicating vendor tests, companies can rely on supplier evidence where appropriate, provided supplier qualification is robust. This reduces redundancy and accelerates deployment timelines.
- Lifecycle Flexibility
CSA aligns better with agile software development. It allows validation practices to evolve with frequent system updates and patches without requiring full revalidation for every release.
Benefits of CSA
Computer Software Assurance (CSA) addresses the limitations of CSV by shifting focus from exhaustive documentation to risk-based, performance-driven validation. The key benefits include:
- Reduced Documentation Burden
CSA minimizes unnecessary paperwork and redirects effort toward testing what matters:
- Focus on performance rather than producing unnecessary records for auditors
- Leaner documentation aligned with risk, not volume
- Faster Implementation
With fewer low-value tasks, projects move forward more quickly:
- Critical functions are tested first, avoiding wasted cycles
- Vendor documentation can be leveraged instead of duplicating effort
- Deployment timelines for new systems are significantly shortened
- Alignment with Agile and Cloud Systems
CSA is built to support modern software environments:
- Works effectively with SaaS platforms and automated updates
- Enables validation of frequent releases without redundant rework
- Fits naturally with agile and iterative development methods
- Improved Assurance of Quality and Safety
By focusing on critical processes, CSA strengthens true system assurance:
- Resources are directed toward patient safety–relevant functions
- Product quality and data integrity are given priority
- Less distraction from low-risk, non-critical features
- FDA Regulatory Endorsement for CSV to CSA
CSA is not just an industry initiative; it stems directly from FDA guidance:
- Reflects the agency’s expectation for a more efficient, risk-based approach
- Provides confidence that a CSA-driven strategy aligns with regulatory priorities
– Advertisement –
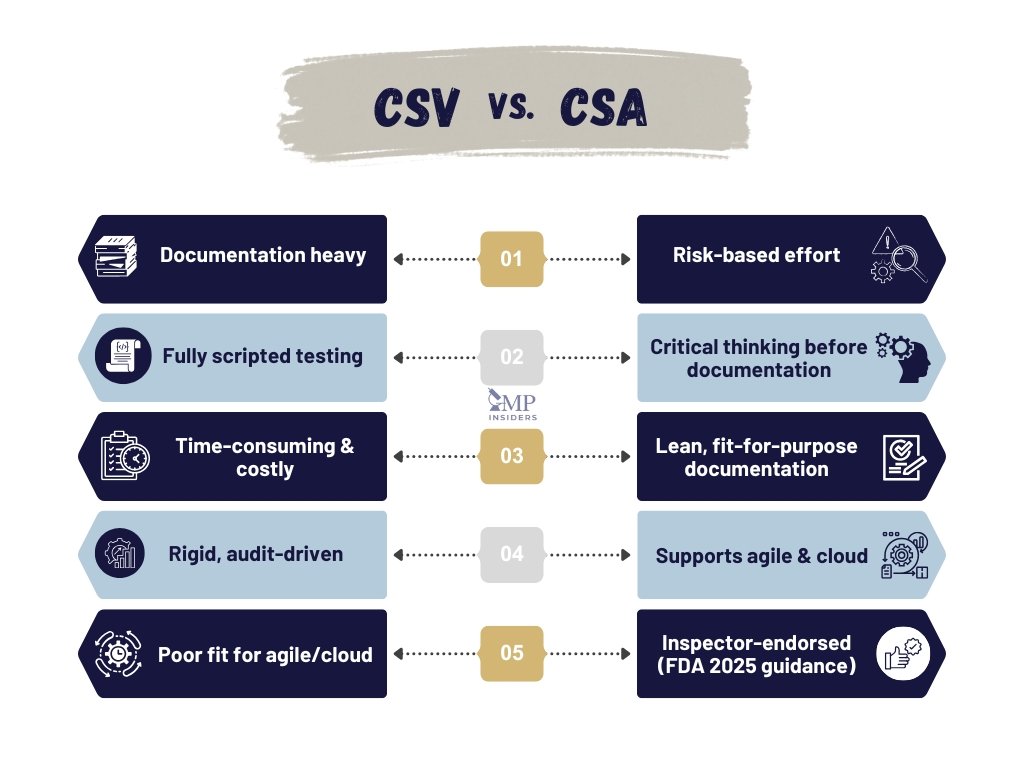
CSV vs CSA: What Is the Difference?
The transition from Computer System Validation (CSV) to Computer Software Assurance (CSA) is not a matter of replacing one framework with another but of shifting emphasis.
CSV relies on exhaustive documentation and scripted testing to demonstrate compliance, whereas CSA applies risk-based assurance, directing effort where it matters most: protecting patients and ensuring product quality.
Objectives
- CSV: Primary objective is to demonstrate compliance through documentation that proves each requirement has been tested.
- CSA: Primary objective is to establish assurance that the system is fit for use, with documentation as supporting evidence rather than the goal.
Documentation Strategy
- CSV: Characterized by detailed protocols, scripts, and reports that often run into thousands of pages. Documentation volume is seen as a proxy for compliance.
- CSA: Documentation is lean and fit-for-purpose. It must be sufficient to defend testing decisions during inspection but avoids redundancy.
Testing Approach
- CSV: Heavily scripted, step-by-step testing of each requirement. While comprehensive, this approach can miss unexpected failures and consumes significant resources.
- CSA: Incorporates a mix of scripted, unscripted, and exploratory testing. High-risk functions receive rigorous testing, while low-risk functions may be tested with less formality. This enables faster identification of system weaknesses.
Use of Vendor Documentation
- CSV: Tends to repeat vendor testing internally, even when suppliers provide validated evidence. This duplication increases workload without improving assurance.
- CSA: Encourages reliance on vendor testing where appropriate, provided supplier qualification and audit evidence confirm the vendor’s credibility.
Alignment with Modern Practices
- CSV: Aligned with traditional, linear software development lifecycles, making it less compatible with frequent updates and agile methods
- CSA: Designed to support agile, cloud-based, and continuously updated systems, allowing validation to adapt with minimal disruption.
| Aspect | CSV | CSA |
|---|---|---|
| Objective | Demonstrate compliance through extensive documentation | Provide assurance that the system is fit for use, focusing on patient safety and product quality |
| Documentation | Heavy, protocol-driven, often thousands of pages | Lean, risk-based, sufficient but not redundant |
| Testing Approach | Fully scripted, step-by-step tests for each function | Combination of scripted and unscripted testing, focused on critical functions |
| Vendor Evidence | Often duplicated internally, regardless of supplier validation | Relies on qualified vendor evidence, reducing duplication |
| Adaptability | Suited to traditional linear development lifecycles | Supports agile, cloud-based, and continuously updated systems |
Transition from CSV to CSA
Adopting CSA is not a simple replacement of templates. It requires rethinking how validation is approached, how risk is assessed, and how documentation is generated. The transition should be treated as a controlled change project that balances regulatory compliance with operational efficiency.
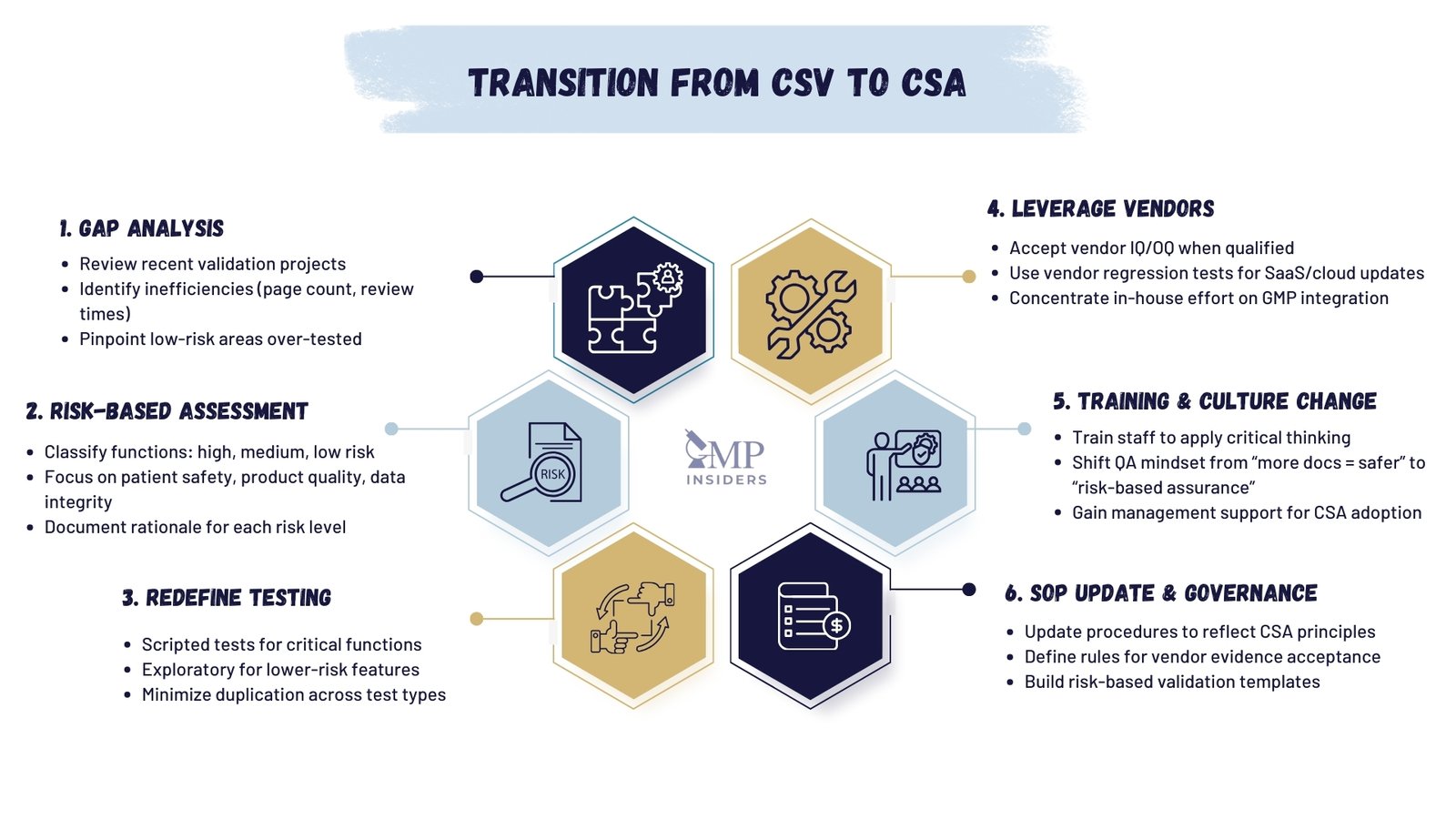
1. Assess Current Validation Practices
A structured gap analysis is the starting point. Companies need to identify where current CSV processes are generating unnecessary effort without adding assurance.
- Review recent validation projects for page count, review times, and number of approvals.
- Identify functions where hundreds of scripted tests were executed for low-risk features (for example, report layout or user interface preferences).
- Map critical systems (MES, LIMS, QMS, EBR) and classify them according to their regulatory impact.
This baseline assessment highlights where CSA principles will have the most immediate benefit.
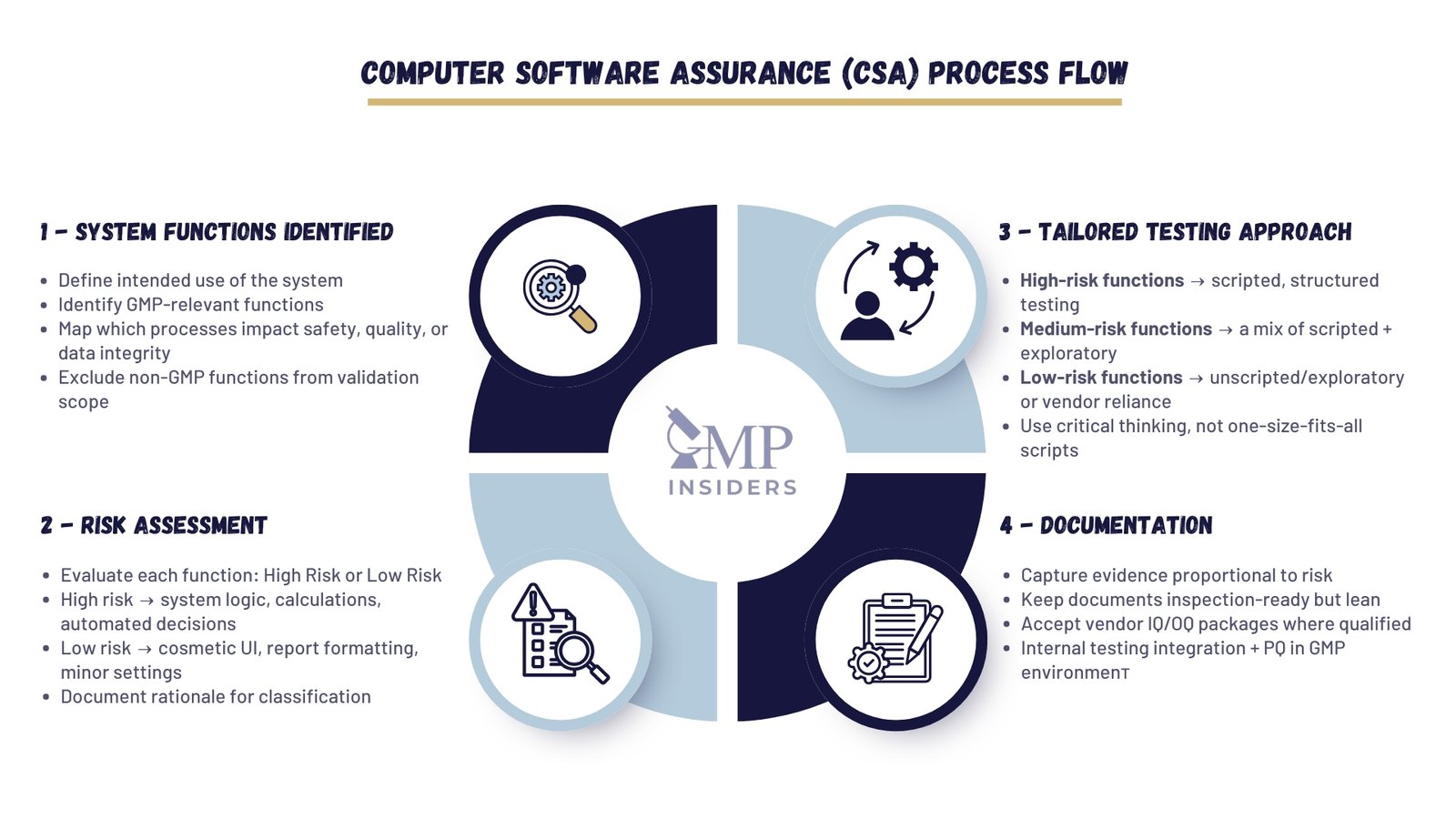
2. Apply Risk-Based Assessment
Risk assessment serves as the foundation of CSA. Each function is examined for its potential impact on:
- Patient Safety: Does Failure Put the Patient at Risk? (e.g., incorrect dose calculation in MES).
- Product quality: Could the system affect sterility, potency, or stability? (e.g., incorrect stability testing logic in LIMS).
- Data integrity: Could data be lost, altered, or misrepresented? (e.g., audit trail manipulation in eQMS).
High-risk functions require structured, documented testing. Low-risk functions may only require exploratory testing or vendor evidence. This proportionality is what differentiates CSA from CSV.
3. Redefine Testing Practices
CSA diversifies how testing is conducted.
- Scripted testing: Still essential for critical functions, such as electronic signature application or automated batch yield calculations.
- Exploratory testing: Applied to lower-risk functions to uncover unexpected issues quickly. Testers are given objectives rather than rigid step-by-step scripts.
- Ad-hoc/unscripted testing: Used where the risk is negligible, such as cosmetic dashboard features.
The outcome is fewer documents but stronger assurance that testing addressed what truly matters.
4. Leverage Vendor Qualification and Evidence
Vendors increasingly provide detailed validation documentation. CSA allows companies to use this evidence instead of duplicating work internally, provided suppliers are qualified.
- Perform supplier qualification audits and document vendor competence.
- Accept vendor IQ/OQ packages for standard configurations.
- Concentrate in-house testing on system integration and PQ in the live GMP environment.
For example, a cloud-based QMS provider may release monthly patches. Instead of re-executing hundreds of scripts, the company can rely on the vendor’s automated regression tests and focus internally on confirming that workflows critical to product release still function.
5. Training and Cultural Change
The biggest challenge in CSA adoption is not technical, but cultural. CSV created an environment where “more documentation” was equated with “better compliance.” Moving away from this mindset requires:
- Training QA, IT, and validation staff to apply critical thinking instead of defaulting to templates.
- Involving senior management to support lean documentation as an acceptable inspection strategy.
- Encouraging inspectors and auditors to review the rationale and risk assessment rather than the thickness of validation binders.
Without cultural change, CSA risks being reduced to “CSV with fewer pages,” rather than a genuine risk-based framework.
6. Update SOPs and Governance
Policies and SOPs must be rewritten to institutionalize CSA. This ensures consistency and inspection readiness.
- Introduce risk-based validation templates that scale with system criticality.
- Define clear rules for when vendor evidence can be accepted.
- Update training matrix to include CSA terminology and principles.
- Establish periodic review cycles to confirm ongoing compliance.
– Advertisement –
Practical Considerations for Transitioning from CSV to CSA
Implementing CSA requires more than technical alignment with FDA guidance. Each department within a pharmaceutical company faces distinct challenges in transitioning from CSV to CSA. Transition success depends on tailoring the approach to laboratories, manufacturing, QA, and IT, while also addressing hybrid environments where both frameworks coexist.
| Department | CSV Limitation | CSA Solution |
|---|---|---|
| QC Lab | Long LIMS go-live | Risk-based testing → faster |
| MES/EBR | Duplicated vendor tests | Leverage vendor IQ/OQ |
| QA | Paper mindset | Focus on risk rationale |
| IT | Disruption from patches | Risk-based updates |
| Hybrid | Inconsistent approach | SOPs define CSV vs CSA |
Quality Control (QC) Laboratories
QC labs rely heavily on computerized systems such as LIMS, CDS, and environmental monitoring tools. Under CSV, validation efforts often consume a significant amount of time, delaying the implementation of new features and upgrades.
Key considerations for labs:
- Risk prioritization:
- High-risk: calculation algorithms, audit trail integrity, stability reporting.
- Low-risk: cosmetic report formatting, color schemes, or display settings.
- Testing strategy: Use a mix of scripted tests for critical calculations and exploratory testing for interface features.
- Efficiency gain: CSA can shorten the go-live time of a new LIMS by focusing on assurance of stability reporting and data transfer, while accepting vendor IQ/OQ for basic functions.
Manufacturing and MES/EBR Systems
Manufacturing Execution Systems (MES) and Electronic Batch Records (EBR) are central to GMP production and carry significant compliance risks. Traditional CSV often requires duplicating vendor validation, delaying production readiness.
Practical CSA application:
- Concentrate scripted testing on batch release logic, equipment integration, and yield calculations.
- Rely on vendor IQ/OQ for basic configuration and system functions.
- Utilize exploratory testing to validate workflow usability in real-world production scenarios.
- Streamline periodic review by focusing on updates that affect validated workflows, not cosmetic changes.
Quality Assurance (QA) Department
QA teams traditionally associate compliance with document volume, making cultural change a critical component. With CSA, QA’s role evolves from approving hundreds of pages to verifying that risk assessments and assurance activities are sound and effective.
Points to consider:
- Mindset shift: Inspectors may initially expect the CSV-style binders; QA must be prepared to confidently explain risk-based rationales.
- Documentation review: QA should verify that testing was appropriate, not that every requirement had a step-by-step script.
- Inspection readiness: Have risk assessments, critical test evidence, and vendor qualification reports organized and defensible.
IT Departments
IT is often responsible for implementing patches, upgrades, and SaaS-based solutions. Under CSV, frequent updates were disruptive because each change triggered revalidation. CSA provides flexibility, but IT must align processes.
Best practices:
- Maintain change management procedures that classify updates by risk (critical vs. non-critical).
- For cloud systems, leverage vendor release notes and regression testing as primary assurance, while performing internal confirmation on critical workflows.
- Collaborate closely with QA to align on the level of testing required per update.
Hybrid Environments
Most companies will not transition to CSA overnight. For years, organizations may run a combination of CSV-validated legacy systems and CSA-aligned new projects.
Challenges and strategies:
- Consistency: Define clear criteria in SOPs for when CSV applies versus CSA.
- Inspector expectations: Be prepared to explain why certain systems still follow CSV.
- Knowledge transfer: Utilize new CSA projects as case studies to train staff and gradually demonstrate their benefits.
- Risk of “CSA-lite”: Avoid reducing documentation without proper risk assessment. Inspectors will challenge lean files if the rationale is not well-documented.
Regulatory Requirements for CSV and CSA
Validation of computerized systems is anchored in international regulatory frameworks. While terminology may differ, the underlying expectation remains consistent: systems that impact product quality, patient safety, or data integrity must be validated in a lifecycle- and risk-based manner.
FDA Guidance on CSV to CSA
The FDA’s 2025 guidance “Computer Software Assurance for Production and Quality System Software” established CSA as the reference framework. It reflects the agency’s intent to reduce the unnecessary burden of validation while maintaining assurance and regulatory compliance.
Key elements include:
- CSV remains acceptable, but CSA is encouraged as a modernized, risk-based framework.
- Testing should be proportional to risk:
- High-risk functions → structured, documented testing.
- Low-risk functions → unscripted or exploratory testing.
- Vendor documentation can be leveraged to reduce duplication.
- The goal is assurance, not volume of documentation.
SEE ALSO: In-Depth Analysis of FDA’s 2025 Guidance on CSA
21 CFR Part 11
This regulation defines the requirements for electronic records and electronic signatures used in FDA-regulated environments. It is the cornerstone of computerized system compliance in the U.S.
- Electronic records must be trustworthy, reliable, and equivalent to paper records
- Validation is required to demonstrate accuracy, reliability, and consistent intended performance
- System controls must include audit trails, security, access management, and record retention
- Electronic signatures must be unique, secure, and legally binding
EU GMP Annex 11 (2011)
Annex 11 of the EU GMP Guide governs computerized systems in Europe. It predates CSA but contains many principles that align with it.
Annex 11 requires:
- Systems supporting GMP activities must be validated and maintained in a validated state throughout their lifecycle.
- Risk management (ICH Q9) must guide the design, validation, and operation of the system.
- Clear control of specifications, testing, and change management
- Defined expectations for audit trails, electronic records, security, and supplier oversight.
Related Article: Annex 11 vs 21 CFR Part 11
Although written in 2011, Annex 11 already pointed toward risk-based control, which CSA now emphasizes more explicitly.
Draft Revision of Annex 11 (2025)
The current draft revision of Annex 11 (published July 2025) expands significantly on the 2011 version. While still under consultation, it confirms the direction regulators are taking.
Highlights include:
- Stronger emphasis on risk management and critical thinking as the basis for validation.
- Expanded sections on data integrity, cybersecurity, access management, and audit trails.
- Alignment with modern IT realities, including cloud platforms, SaaS models, and agile development.
- Greater clarity on supplier management and vendor qualification.
This revision does not replace CSA but demonstrates how EU and FDA expectations are converging.
FAQ: CSV vs CSA
Can a Company Apply CSA Principles Retroactively To Legacy CSV-Validated Systems?
Yes, CSA principles can be applied to legacy systems, but companies must approach this carefully. The first step is to reassess critical functions and determine if the current validation effort aligns with their risk level.
In many cases, redundant testing and excessive documentation can be reduced without compromising compliance. Inspectors will accept this if the rationale is well-documented and the risk assessments are defensible.
Does CSA Eliminate the Need for Protocols Like IQ, OQ, and PQ?
CSA does not eliminate IQ, OQ, or PQ, but it changes how they are applied. Instead of blindly executing every step, the effort is proportionate to the criticality of the function being tested.
For example, IQ for infrastructure may rely heavily on vendor documentation, while PQ for critical batch-release functions may remain highly detailed. The lifecycle remains, but the emphasis shifts from justification to volume.
How Do Inspectors View CSA During Audits?
Inspectors expect CSA to be applied in a structured, risk-based manner. They will focus on whether the company can justify why certain tests were done and why others were not. A lean validation file is acceptable if the reasoning is clearly documented. In practice, inspectors may challenge weak risk assessments more than missing documents.
Can CSA Be Applied To Cloud-Based And SaaS Systems?
Yes, CSA is particularly well-suited for cloud and SaaS environments where frequent updates are common. Instead of revalidating the entire system after every patch, risk-based assessments determine which functions require testing.
Vendor regression testing can be accepted if the supplier is qualified and meets the requirements. Internal testing then focuses on business-critical workflows that impact product release and patient safety.
Can CSA Be Combined With Traditional CSV in the Same Company?
Yes, most companies operate hybrid environments during the transition. Legacy systems may remain under CSV until their next major change, while new systems adopt CSA. Clear SOPs must define when CSV applies and when CSA is acceptable. This hybrid approach helps avoid compliance gaps and ensures a smooth cultural transition.
How Does CSA Handle Frequent Software Updates?
CSA allows companies to classify updates based on risk. Critical changes, such as algorithm modifications, require formal validation, while low-risk patches may only need confirmation testing.
Vendor release notes and automated regression tests play a central role in demonstrating assurance. This approach reduces downtime and accelerates the implementation of updates.
Does CSA Require New Types Of SOPs?
Yes, SOPs must be updated to reflect CSA principles. These include procedures for risk assessment, vendor qualification, exploratory testing, and lean documentation practices. Existing SOPs focused on CSVs may be too rigid and should be revised. Without updated SOPs, inspectors may question the consistency of CSA implementation.
Final Thoughts
Computer System Validation has served the industry for decades as the foundation for demonstrating compliance of computerized systems. Its structured, documentation-heavy approach provided consistency but often created inefficiencies that slowed system implementation and diverted focus away from product quality.
Computer Software Assurance addresses these limitations by reorienting validation around risk, critical thinking, and efficient testing. It does not replace CSV entirely but refines how the validation effort is allocated.
By focusing on functions that directly impact patient safety, product quality, and data integrity, CSA assures a reduced administrative burden.
Regulators, including the FDA and the European Commission, are converging on this risk-based model through Annex 11. For companies, the challenge is cultural as much as procedural: success requires strong risk assessments, updated governance, and staff prepared to defend assurance-based decisions during inspection.
CSV remains relevant in specific contexts, but CSA sets the direction for the future. Organizations that adapt early will not only reduce compliance overhead but also position themselves to adopt new technologies more quickly, with confidence that systems remain under control and inspection-ready.
Disclaimer: This article includes advertisement placements in collaboration with Validify. The editorial content was created independently by GMP Insiders.














