Computer System Validation (CSV) demonstrates that computerized systems used in GxP environments consistently function as intended and comply with regulatory requirements. Its purpose is to ensure the reliability of data, to protect product quality, and ultimately, patient safety.
Risk management defines the way CSV is planned, executed, and maintained. Instead of applying the same level of validation effort to every function, companies are now expected to scale their approach based on the potential impact of each system or function on GxP compliance, product quality, and data integrity.
Guidelines such as ICH Q9 (R1) on Quality Risk Management, GAMP 5 (Second Edition), and FDA’s 21 CFR Part 11 already underline the importance of proportional validation strategies.
The draft update of EU GMP Annex 11 (2025) reinforces this direction further by explicitly addressing data governance, cybersecurity, cloud services, and even AI/ML applications. Together, these frameworks signal a clear expectation: CSV must be managed as a continuous, risk-based lifecycle process rather than a one-time documentation exercise.
Traditional vs Risk-Based Approach in CSV
The way Computer System Validation is applied has changed significantly. Traditional methods treated every system function with the same level of scrutiny, while the modern risk-based approach tailors validation effort to the potential impact on GxP processes, product quality, and patient safety.
| Aspect | Traditional CSV | Risk-Based CSV |
|---|---|---|
| Validation scope | Same level of testing for all functions | Testing scaled to system and function criticality |
| Documentation | Extensive, volume-driven | Focused, risk-justified |
| Testing effort | Exhaustive scripted tests | Proportional scripted/exploratory testing |
| Resource use | High cost, long timelines | Optimized effort, shorter cycles |
| Regulatory alignment | Meets minimum compliance | Fully aligned with ICH Q9, GAMP 5, Annex 11 draft, CSA |
– Advertisement –
Traditional CSV
Traditional validation was designed to demonstrate compliance through volume of documentation and exhaustive testing. While thorough in appearance, it often misallocated resources.
Key characteristics included:
- Uniform testing of both critical and non-critical functions.
- Heavy reliance on scripted test cases, regardless of risk.
- Documentation that prioritized quantity over relevance.
This approach led to:
- Long and costly validation cycles.
- Reduced flexibility when introducing changes or upgrades.
- Limited focus on areas where system failures could directly affect compliance.
Related Article: CSV in Pharmaceutical Industry
Risk-Based CSV
Risk-based validation introduces proportionality. Testing and documentation are scaled according to the criticality of the function or process, ensuring that effort is concentrated where failures would have the highest impact.
Its main advantages are:
- Targeted testing that prioritizes functions critical to product quality and data integrity.
- Documentation that demonstrates decision-making and risk rationale rather than sheer volume.
- Shorter validation timelines without compromising compliance.
- Alignment with regulatory expectations under ICH Q9, GAMP 5, FDA CSA, and the draft Annex 11 update.
Foundations of Quality Risk Management in CSV
Quality Risk Management provides the framework for aligning Computer System Validation (CSV) with regulatory expectations in the pharmaceutical industry. It ensures that validation activities are proportional to the risks posed by the system, rather than uniformly applied across all functions.
The aim is to direct resources where failures could have the most significant impact on patient safety, product quality, and data integrity.
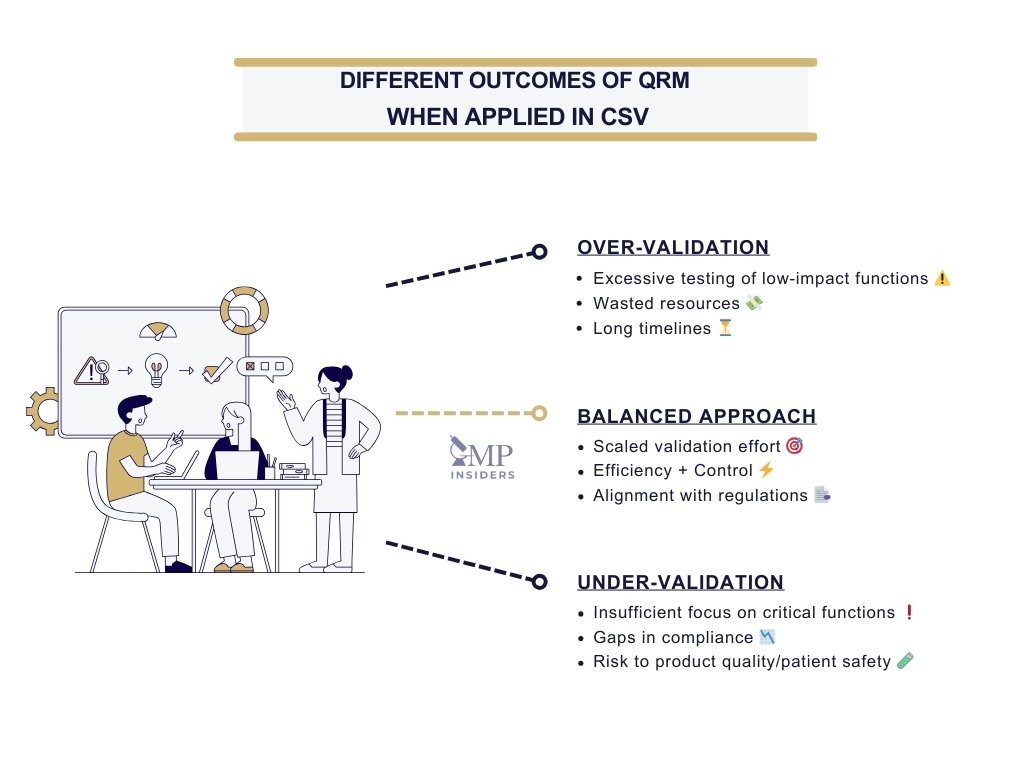
Without structured risk management, organizations risk two extremes:
- Over-validation: excessive testing of low-impact functions, leading to wasted resources and long timelines.
- Under-validation: insufficient attention to critical functions, leaving vulnerabilities that inspectors can easily identify.
By embedding risk management into CSV, companies demonstrate control, efficiency, and regulatory alignment.
ICH Q9: Quality Risk Management Principles
The revised ICH Q9 (R1) serves as the global standard for implementing risk management in GxP environments. It defines a systematic process that applies directly to computerized systems.
Key stages include:
- Risk assessment
- Identify potential hazards in system design and operation.
- Evaluate the likelihood of occurrence, the severity of impact, and the ability to detect the failure.
- Example: a calculation algorithm in LIMS has a direct impact on product release data and therefore carries a higher risk than a reporting layout.
- Risk control
- Define mitigation measures such as additional testing, procedural safeguards, or supplier qualification.
- Establish acceptance criteria for residual risk.
- Ensure controls are proportionate: not every risk needs the same level of action.
- Risk review
- Reassess risks periodically and whenever systems undergo change.
- Account for evolving regulatory expectations and technological updates.
- Document findings to demonstrate continuous oversight.
- Risk communication
- Record risk rationale in validation deliverables like the URS, VMP, and traceability matrix.
- Communicate decisions across teams (QA, IT, QC) to maintain consistency.
ICH Q9 ensures that risk management in CSV is structured, transparent, and auditable.
SEE ALSO: Quality Risk Management in Pharmaceutical Industry
GAMP 5 Risk-Based Lifecycle
GAMP 5 (Second Edition) operationalizes ICH Q9 principles for computerized systems. It provides a lifecycle model that integrates risk management into every phase, from concept to retirement.
Core principles include:
- Fit for intended use – validation must demonstrate that the system performs as required to support GxP processes.
- Five-step risk process:
- Define the system and its intended use.
- Identify potential risks (technical failures, functional issues, supplier dependencies).
- Assess risks using structured methods such as functional risk assessments.
- Control risks through testing, procedures, or supplier oversight.
- Review risks regularly throughout the system lifecycle.
- Software categorization – tailoring validation effort based on whether the software is custom-built, configurable, or commercial off-the-shelf.
- Functional Risk Assessments (FRA) – analyzing each system function for its impact on patient safety, product quality, and data integrity.
FRA rankings commonly use scales such as:
- High – failures directly affect GxP processes or data integrity (e.g., batch release calculations).
- Medium – failures indirectly affect quality but are detectable (e.g., audit trail reporting).
- Low – failures have minimal or no impact (e.g., screen layout preferences).
The outcome of an FRA drives testing strategy: high-risk = detailed scripted tests, medium-risk = semi-scripted or exploratory testing, low-risk = basic verification or reliance on supplier documentation.
Related Article: GAMP 5 Impact in CSV
Critical Thinking in Risk Management
Risk management frameworks provide structure, but critical thinking is required to apply them effectively. Regulators increasingly emphasize that companies must demonstrate reasoning, not just produce filled-out templates.
Key elements of critical thinking in CSV:
- Focus on intended use: how the system supports specific GxP processes.
- Consider user interaction: points where human error may combine with system weaknesses.
- Prioritize risks that directly impact data integrity and patient safety.
- Avoid wasting effort on functions that have no quality impact, even if they are technically complex.
- Document not only what was decided, but why it was decided.
A risk assessment that lacks justification is vulnerable during inspections. Inspectors expect to see that risk-based decisions are evidence-driven, well-documented, and consistently applied.
CSV Risk Assessment Methods
Risk assessment is the central activity that translates risk management principles into actionable validation strategies. In Computer System Validation, it determines which functions require intensive testing, what documentation is necessary, and how risks should be mitigated. A structured approach ensures consistency, transparency, and regulatory acceptance.
| Method | Focus | Scoring | Best Use |
|---|---|---|---|
| FRA | Function impact | High/Med/Low | URS/design |
| FMEA | Failures + prioritization | S × O × D | Complex systems |
| HACCP | Hazards + controls | Critical points | Data integrity & cybersecurity |
Functional Risk Assessment (FRA) in CSV
The Functional Risk Assessment (FRA) is a practical tool promoted in GAMP 5 training. It evaluates each function of a computerized system based on its potential GxP impact.
- High-risk functions → direct impact on patient safety, product quality, or data integrity. Example: calculation of potency results in a Laboratory Information Management System (LIMS).
- Medium-risk functions → indirect impact, often detectable by other controls.
Example: automatic generation of certificates of analysis. - Low-risk functions → minimal or no impact on regulated processes.
Example: screen customization or display themes.
How FRA is applied:
- Each function is reviewed during URS and design phases.
- Functions are ranked (High/Medium/Low or numeric scales).
- Ranking drives testing strategy and documentation effort.
Failure Mode and Effects Analysis (FMEA)
FMEA is one of the most widely used methods for structured risk assessment in CSV. It evaluates potential failure modes and prioritizes them based on three factors:
- Severity (S): How serious the impact would be on patient safety, product quality, or data integrity.
- Occurrence (O): The likelihood of the failure happening.
- Detectability (D): The ability to detect the failure before it causes harm.
The combination of these factors produces a Risk Priority Number (RPN):
RPN=S×O×D
Functions or processes with the highest RPN are prioritized for testing, controls, or procedural safeguards.
Advantages of FMEA in CSV:
- Provides a structured, quantifiable approach.
- Easy to explain to auditors and inspectors.
- Integrates well with change control and periodic review processes.
Hazard Analysis and Critical Control Points (HACCP)
Although HACCP is traditionally used in manufacturing, its principles are also applied in computerized systems:
- Identify potential hazards in system operation (e.g., data corruption, unauthorized access).
- Define critical control points where controls must be applied to prevent or detect hazards.
- Establish monitoring and corrective actions for each control point.
HACCP is beneficial when CSV is linked to data integrity and cybersecurity risks, as it forces teams to identify and manage failure points in data flow.
Initial Risk Assessment in CSV
The initial risk assessment is performed at the earliest stages of Computer System Validation. Its purpose is to identify which system functions have a direct impact on GxP processes, product quality, and data integrity. At this point, risk classification tools such as Functional Risk Assessment (FRA) or FMEA are used to rank requirements as high, medium, or low risk.
This assessment provides the foundation for the validation plan:
- High-risk functions are linked to detailed, scripted testing
- Medium-risk functions are verified with semi-scripted or exploratory tests
- Low-risk functions may rely on supplier documentation or minimal verification
By performing a thorough initial risk assessment, companies ensure that validation resources are allocated proportionally and can demonstrate regulatory justification for their approach.
Risk Ranking and Filtering
Not all risks require the same level of control. Risk ranking and filtering methods allow teams to classify and prioritize risks systematically.
Common approaches include:
- Qualitative scales (High/Medium/Low) – simple and effective for FRA.
- Quantitative scoring (e.g., 1–5 for severity, occurrence, detectability) – often used in FMEA.
- Combined approaches – using scoring to support ranking decisions.
Outputs of risk ranking:
- Focused testing for high-priority risks.
- Documented rationale for why low-priority risks require limited or no additional action.
- Clear traceability from URS to test protocols.
Risk Mitigation and Control Strategies
Once risks are identified and ranked, appropriate mitigation strategies must be applied. These can include:
- Enhanced testing of critical functions.
- Procedural controls such as SOPs, double-checks, or restricted access.
- Supplier qualification when relying on third-party systems.
- Automation tools to reduce human error in testing and reporting.
- System configuration restrictions to prevent unauthorized changes.
Risk control decisions must always be documented, showing how residual risk was accepted or reduced to an acceptable level.
– Advertisement –
Implementing a Risk-Based Approach in CSV
Risk management in CSV is not limited to theoretical assessments. It must be embedded in every stage of the validation lifecycle, from initial planning through system operation and retirement. A risk-based approach ensures that validation resources are focused on functions that directly affect GxP compliance.
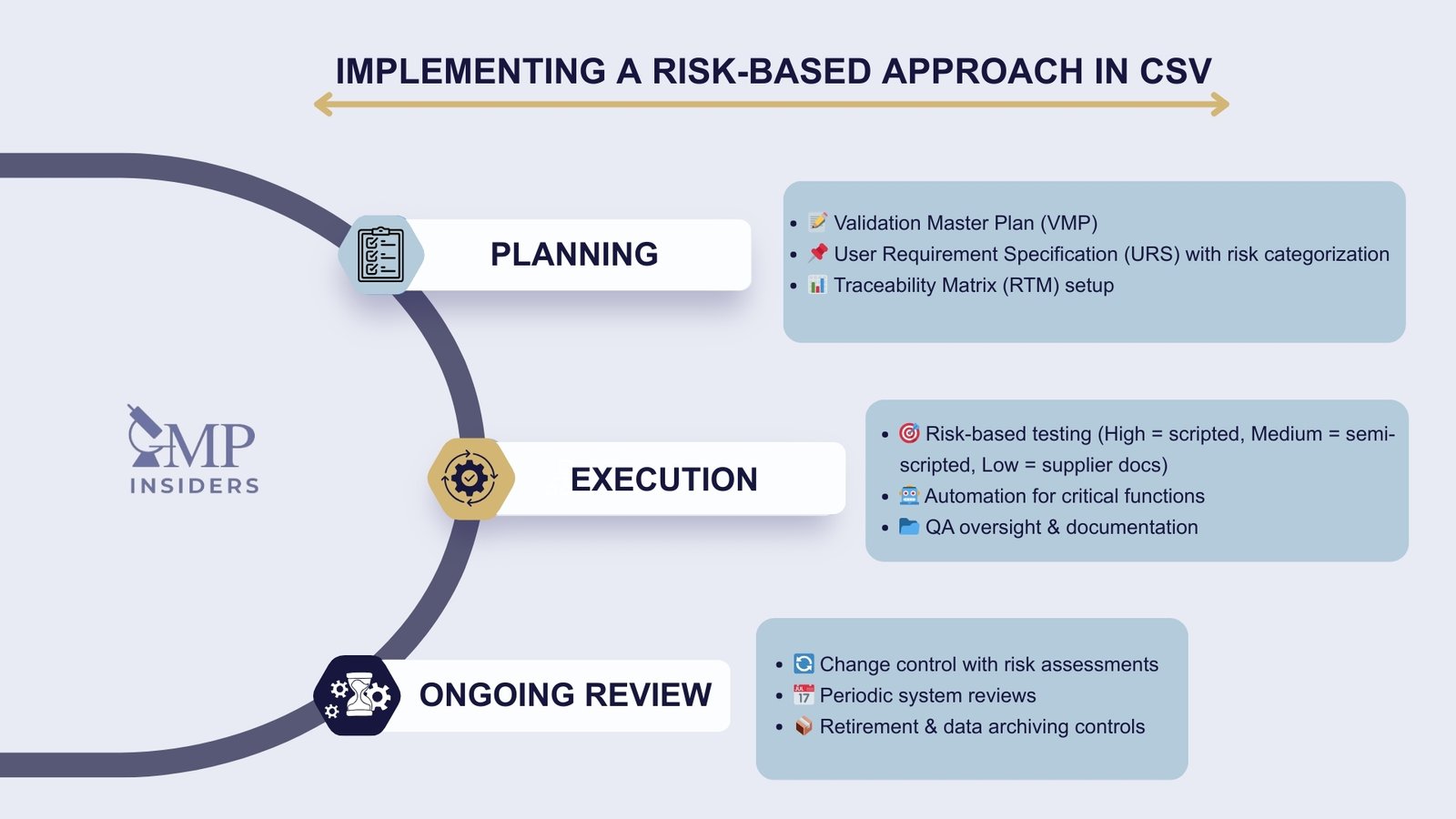
Risk-Based Planning
The planning stage defines the scope of validation and sets the framework for applying risk principles.
- Validation Master Plan (VMP):
- Outlines the overall approach to validation, explicitly describing how risk management will be applied.
- Defines acceptance criteria for system risks.
- Identifies responsibilities across QA, IT, and user departments.
- User Requirement Specification (URS):
- Requirements categorized by impact on GxP processes.
- High-risk requirements linked to specific validation deliverables.
- Each URS entry includes documented risk rationale.
- Traceability Matrix (RTM):
- Links requirements to risk assessments and test cases.
- Demonstrates that all high- and medium-risk functions are adequately verified.
- Provides inspectors with clear visibility of risk-based decision-making.
Risk-Based Execution
During execution, the level of testing is scaled to the criticality of the system function.
- High-risk functions:
- Require scripted, detailed test protocols.
- Evidence of test results must be complete, reviewed, and approved by QA.
- Medium-risk functions:
- May be verified with semi-scripted or exploratory testing.
- Supporting documentation is lighter but still demonstrates adequacy.
- Low-risk functions:
- Verified by basic functionality checks or reliance on supplier documentation.
- Minimal effort justified with a documented rationale in the risk assessment.
- Automation and tools:
- The use of automated testing tools for repetitive, high-risk functions reduces human error.
- Electronic validation platforms facilitate the management of traceability and approvals.
CSV Assessment Test
A CSV assessment test is the execution phase where validation activities confirm that system functions operate as intended according to their risk classification. Unlike traditional validation, where every function receives the same level of testing, a risk-based CSV assessment test adapts test intensity to criticality.
- High-risk functions: require comprehensive scripted protocols with complete evidence and QA oversight.
- Medium-risk functions: may be tested using semi-scripted or exploratory methods that confirm compliance without unnecessary repetition.
- Low-risk functions: may be verified through supplier qualification evidence or light functional checks.
The CSV assessment test ensures that testing is scientific, risk-justified, and traceable to the URS and risk assessment. This not only satisfies regulators but also prevents resources from being consumed on low-value testing activities.
Ongoing Risk Review
Validation does not end after system release. Risk-based CSV requires continuous monitoring and reassessment throughout the lifecycle.
- Periodic reviews:
- Frequency depends on system criticality and the history of issues.
- Focus on verifying that risk controls remain effective.
- Change control:
- Every system change (patch, upgrade, configuration update) must include a documented risk assessment.
- Testing scope adjusted according to the risk introduced by the change.
- System retirement:
- Risks assessed during decommissioning, including data migration and archiving.
- Validation evidence maintained to show regulatory compliance beyond system use.
Regulatory Framework and Current Developments
Authorities have incorporated risk management principles into their guidelines, requiring companies to justify the scope and decisions of their validation through structured methods.
ICH Q9 (R1) – Quality Risk Management
- Establishes the formal risk management process used across the pharmaceutical industry.
- Four stages (assessment, control, review, and communication) provide the backbone for CSV risk activities.
- Revised in 2023 (R1) to clarify concepts such as risk-based decision-making and subjectivity in assessments.
- Directly supports risk-based CSV by ensuring proportional validation activities.
GAMP 5 (Second Edition)
- Practical framework for applying ICH Q9 principles to computerized systems.
- The lifecycle model integrates risk evaluation from concept to retirement.
- Key features:
- Fit for intended use as the validation goal.
- A five-step risk process is embedded throughout the lifecycle.
- Software categories guiding depth of validation.
- Functional Risk Assessments (FRA) to classify functions as high, medium, or low risk.
- Widely recognized by regulators as the de facto best practice for CSV.
EU GMP Annex 11 – Current vs Draft Update (2025)
- Current version (2011):
- Sets expectations for validation, documentation, supplier management, and periodic review.
- Requires risk management to be applied in proportion to the impact of computerized systems on product quality.
- Draft update (2025):
- Stronger emphasis on risk-based lifecycle management.
- Explicit requirements for data governance and digitalization.
- Clearer distinction between user and supplier responsibilities.
- Expanded coverage of cloud-based solutions, cybersecurity, and AI/ML systems.
- Reinforces the need for continuous risk assessment, not one-off validation.
FDA 21 CFR Part 11
- Governs electronic records and electronic signatures in GxP environments.
- Requires that systems handling regulated data are validated for accuracy, reliability, and consistent performance.
- FDA supports a risk-based approach in CSV through its Computer Software Assurance (CSA) initiative, which emphasizes:
- Testing proportional to risk.
- Critical thinking in validation decisions.
- Reduced reliance on excessive scripted testing.
Related Article: CSV vs CSA in Software Validation
Common Pitfalls in Risk-Based CSV
Although risk-based CSV is widely accepted and encouraged by regulators, many organizations struggle with its implementation. Typical pitfalls arise when risk management is applied superficially or inconsistently, resulting in weak validation evidence or wasted resources.
Over-Documentation
- Treating risk-based CSV as another layer of paperwork instead of a way to optimize effort.
- Generating unnecessary test cases for non-critical functions.
- Producing large volumes of evidence that lack focus and add little regulatory value.
– Advertisement –
Poorly Justified Risk Assessments
- Copy-paste risk assessments without context or rationale.
- FRA, FMEA, or matrices completed mechanically, without clear links to system functions.
- Lack of transparency in how risk ratings were assigned (e.g., why a function is “medium” instead of “high”).
Inadequate Supplier Oversight
- Over-reliance on vendor-supplied documentation without verifying its adequacy.
- Missing supplier audits for critical GxP systems.
- Failing to define responsibilities between supplier and user in validation activities.
Treating Validation as a One-Off Activity
- Conducting a risk assessment only at system implementation, but not updating it during changes or reviews.
- Ignoring lifecycle risk management, especially during upgrades, patches, or decommissioning.
- Lack of periodic review processes to confirm that risk controls remain effective.
Lack of Critical Thinking
- Following templates without evaluating intended use or actual GxP impact.
- Testing functions in detail simply because they are technically complex, even if they have no quality relevance.
- Failing to justify why certain risks require limited action.
Future Outlook for Quality Risk Management in CSV
The application of risk management in Computer System Validation will continue to evolve as technology, regulatory expectations, and industry practices advance. Several trends are likely to shape the future of CSV:
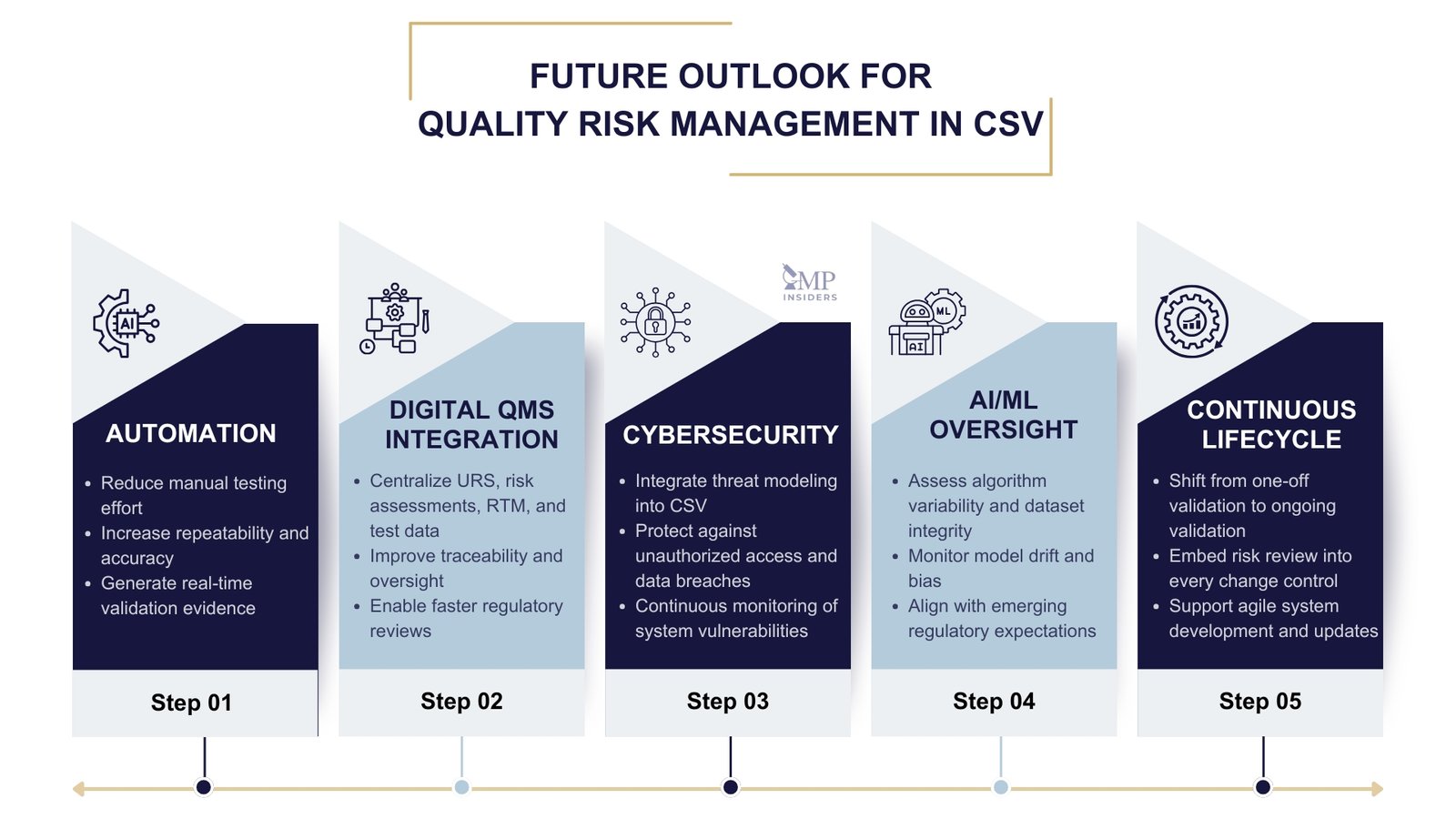
- Increased automation of validation activities: Risk-based testing will benefit from automated verification tools that reduce manual effort, improve accuracy, and generate real-time evidence for inspectors.
- Integration with digital quality systems: Validation data will increasingly be managed through electronic platforms that connect URS, risk assessments, traceability matrices, and test records in one environment. This will streamline oversight and enhance transparency.
- Focus on data integrity and cybersecurity: With growing reliance on cloud systems and interconnected platforms, risk management will expand to include cybersecurity threat modeling and continuous monitoring. Annex 11’s draft update signals this as a clear regulatory direction.
- AI and machine learning oversight: As AI-driven systems enter GxP processes, risk assessments will need to account for algorithm variability, dataset integrity, and model drift. Regulators are beginning to publish expectations in this area, making it a critical focus for future CSV strategies.
- Continuous validation mindset: CSV will increasingly be viewed as a lifecycle activity with continuous updates, rather than a project milestone. This aligns with agile system development and regulatory expectations for ongoing risk review.
Looking ahead, risk management will not only improve regulatory compliance but also drive efficiency, resilience, and adaptability in pharmaceutical computerized systems. Companies that embed risk-based thinking into every stage of system validation will be better prepared for technological change and regulatory scrutiny.
FAQ
How Does Risk Management Apply to Cloud-Based Systems?
Cloud solutions introduce risks related to data availability, security, and compliance. Risk assessments in CSV must address supplier responsibilities, service-level agreements, and data backup strategies.
Regulators expect clear evidence that users retain oversight of critical functions, even when hosted externally. Mitigation may include supplier audits, penetration testing, or redundant data storage.
How Should Electronic Audit Trails Be Handled in Risk Assessments?
Audit trails are a primary control for data integrity. Risk assessments must evaluate whether audit trails capture all critical actions, are secure from manipulation, and can be reviewed effectively. Missing or weak audit trails represent high risk and require additional testing or procedural safeguards. Regulators increasingly inspect audit trail functionality in detail.
What Is the Link Between Cybersecurity and CSV Risk Management?
Cybersecurity threats directly affect data integrity and system availability. Risk assessments must consider external attacks, malware, and unauthorized access as potential hazards. Controls may include encryption, intrusion detection, and multi-factor authentication. Annex 11’s draft update explicitly reinforces the integration of cybersecurity into CSV.
How Are Configurable Off-The-Shelf Systems Treated in Risk-Based CSV?
Configurable systems pose a higher risk than pure off-the-shelf products because configuration changes can affect compliance functions. Risk management identifies which configurations impact product quality or records and ensures they are validated.
Vendor-supplied evidence may be leveraged, but must be supplemented with user-specific testing. Documentation should clearly distinguish standard functionality from configured features.
How Often Should Risk Assessments Be Updated During System Operation?
Risk assessments must be reviewed periodically and whenever significant changes occur. The frequency depends on the system’s criticality and history of issues, but annual reviews are common practice. Updates are mandatory after patches, upgrades, or changes to system use. Regulators expect to see a documented process for ongoing risk monitoring.
Can Automated Testing Reduce CSV Risks?
Yes, automated testing reduces human error and increases repeatability in high-risk functions. Risk assessments should determine where automation is appropriate, such as regression testing of critical calculations. However, the automated tools themselves may require validation. Proper documentation ensures inspectors can trust the computerized evidence.
Final Thoughts
Risk management is no longer an optional add-on in Computer System Validation; it is the framework regulators expect companies to follow. By applying structured methods such as Functional Risk Assessments, FMEA, and risk ranking, organizations can scale validation activities according to the impact on GxP processes.
Guidelines, including ICH Q9 (R1), GAMP 5 (Second Edition), FDA 21 CFR Part 11, and the draft revision of EU GMP Annex 11, confirm the global shift toward lifecycle-driven, risk-based validation. Companies that implement these principles demonstrate control, efficiency, and readiness for inspection.
Ultimately, risk-based CSV delivers more than compliance. It ensures that computerized systems remain reliable, data remains trustworthy, and pharmaceutical products reach patients with the highest standards of quality and safety.
Disclaimer: This article includes advertisement placements in collaboration with Validify. The editorial content was created independently by GMP Insiders.














