Computerized systems are now embedded in nearly every aspect of pharmaceutical manufacturing and quality operations. From electronic batch records and laboratory information management systems to automated production equipment, they enable efficiency, consistency, and reliability in delivering safe and effective medicines.
Computer System Validation (CSV) provides a structured approach to demonstrate and document that computerized systems perform as intended across their entire lifecycle.
Regulatory authorities, such as the U.S. FDA under 21 CFR Part 11 and the European Medicines Agency under EU GMP Annex 11, require the validation of systems that impact product quality, patient safety, or data integrity.
This article presents a structured overview of CSV in the pharmaceutical industry. It examines what defines a computerized system, the regulatory framework, and the role of GAMP 5 as a practical guide.
It also explores the lifecycle process, documentation requirements, and common implementation challenges, while addressing emerging trends such as Computer Software Assurance (CSA) that signal a shift toward more agile and risk-based validation practices.
What Is a Computerized System?
In the pharmaceutical industry, a computerized system is defined as a combination of software, hardware, and associated procedures that together fulfill specific functions supporting GMP activities.
According to EU GMP Annex 11, a computerized system is “a set of software and hardware components which together fulfill certain functionalities”. The system also includes any associated equipment, documentation, and trained personnel required for its operation.
Computerized systems are widely used across pharmaceutical operations, including:
- Manufacturing systems such as Distributed Control Systems (DCS), Supervisory Control and Data Acquisition (SCADA), and Manufacturing Execution Systems (MES).
- Laboratory systems such as Chromatography Data Systems (CDS), Laboratory Information Management Systems (LIMS), and standalone analytical instrument software.
- Quality and compliance systems such as Document Management Systems (DMS), Electronic Batch Records (EBR), Training Management Systems, and Pharmacovigilance databases.
The scope of what constitutes a computerized system is therefore broad, extending well beyond complex enterprise software to include standalone instruments and smaller applications that directly or indirectly impact product quality, data integrity, or patient safety.
Key Components of a Computerized System
For a system to function reliably and remain compliant with GMP expectations, each component must be clearly understood, well-controlled, and maintained throughout its lifecycle. These components are typically described as hardware, software, data, processes, and people.
| Component | What It Is | Why It Matters in GMP |
|---|---|---|
| Hardware | The physical layer of the system: servers, workstations, network devices, and peripherals like printers and scanners. | Provides the foundation for running applications and handling GMP data securely and reliably. |
| Software | Programs that drive the system, from operating systems to specialized GMP applications such as LIMS, CDS, or MES. | Ensures processes are executed correctly, data is processed accurately, and regulatory requirements are met. |
| Data | The information created, stored, and used by the system, including inputs, records, and outputs. | Must remain accurate, complete, and secure to uphold data integrity and support regulatory compliance. |
| Processes | SOPs, guidelines, and routines that govern how the system is operated, maintained, and secured. | Keep system use consistent, controlled, and compliant with GMP expectations. |
| People | Users, administrators, and support staff who interact with and manage the system. | Proper training and defined responsibilities reduce errors and safeguard the validated state of the system. |
What Is Computer System Validation (CSV)?
Computer System Validation (CSV) is the documented process of demonstrating that a computerized system is installed, operated, and maintained in a way that consistently produces reliable results in line with defined regulatory requirements.
The purpose of CSV is to provide assurance, supported by objective evidence, that a computerized system performs its intended functions. This assurance is essential because even minor errors in such systems can lead to incorrect analytical results, deviations in manufacturing processes, or compromised regulatory data, all of which represent significant compliance and safety risks.
Unlike general software testing, CSV follows a lifecycle approach. It begins with defining the system’s intended use and continues through design, qualification, operational use, maintenance, and eventual retirement.
At each stage, documented evidence is required to confirm that the system functions as expected and that risks to compliance and data integrity are identified, mitigated, and controlled.
The key objectives of CSV are to:
- Verify that the system is suitable for its intended use and aligned with user and regulatory requirements.
- Protect data integrity by ensuring that electronic records are accurate, consistent, complete, and secure.
- Demonstrate compliance with applicable regulations, including FDA 21 CFR Part 11, EU GMP Annex 11, and ICH Q9 on Quality Risk Management.
- Support patient safety by reducing the likelihood of errors in manufacturing, testing, and product release.
Well-executed CSV establishes confidence in computerized systems, reduces the risk of regulatory observations, and supports efficient and compliant pharmaceutical operations. It is therefore regarded not only as a regulatory requirement but also as a fundamental element of good manufacturing practice.
New Requirements in Annex 11 (Draft Revision)
The draft revision of EU GMP Annex 11 strengthens CSV expectations, expanding from a brief five-page guideline into a more detailed document with 17 sections. Key enhancements include:
- Integration with the Pharmaceutical Quality System (PQS): CSV is no longer treated as an isolated IT activity; senior management oversight and quality governance are explicitly required.
- Expanded Role of Risk Management: QRM principles must be applied throughout the lifecycle, ensuring that the depth of validation is proportionate to the system’s risk.
- Cybersecurity and Technical Controls: New clauses require documented measures for firewalls, patch management, antivirus, penetration testing, backup, and disaster recovery.
- Audit Trails and Electronic Signatures: More detailed requirements specify how audit trails should be configured, reviewed, and maintained, with expanded coverage of hybrid systems and alignment to 21 CFR Part 11.
- Periodic Reviews: Now explicitly required, with clear guidance on scope and expectations to ensure systems remain validated.
- Data Handling and Archiving: Dedicated requirements for ensuring integrity, backup, and secure long-term storage of GMP data.
These updates reflect the evolution of digital technologies, cloud adoption, and the growing challenges of cybersecurity. For pharmaceutical companies, the revised Annex 11 underscores the need to embed CSV within the broader PQS, adopt proactive risk management, and maintain continuous oversight of computerized systems.
The GAMP 5 Framework: A Risk-Based Approach
While regulatory guidelines such as FDA 21 CFR Part 11 and EU GMP Annex 11 define what must be achieved when validating computerized systems, they do not prescribe how to achieve it.
To fill this gap, the industry relies on the Good Automated Manufacturing Practice (GAMP) 5 guide, published by the International Society for Pharmaceutical Engineering (ISPE). GAMP 5 is not a regulation but is considered the global standard for implementing Computer System Validation in a structured and risk-based manner.
At its core, GAMP 5 promotes a lifecycle approach to computerized systems, ensuring that validation activities extend from initial concept through decommissioning. It emphasizes that the depth and extent of validation should be commensurate with the risk the system poses to product quality, patient safety, and data integrity.
This principle allows companies to focus their efforts where it matters most, while avoiding unnecessary documentation for lower-risk functions.
System Categorization
GAMP 5 introduces a widely used model for categorizing systems and software according to their complexity and impact. Categories range from simple infrastructure (e.g., operating systems, databases) to configurable or bespoke applications. This categorization helps determine the appropriate level of validation effort.
- Category 1: Infrastructure software, including operating systems and database management tools.
- Category 3: Non-configurable commercial software used as-is.
- Category 4: Configured software, where standard applications are tailored to meet user needs.
- Category 5: Bespoke or custom-developed software, requiring the highest level of validation.
Supplier Involvement
A key principle of GAMP 5 is effective collaboration with suppliers and service providers. Since many systems are purchased commercially rather than developed in-house, leveraging vendor testing, documentation, and quality certifications can significantly reduce the validation burden.
Regulators accept this approach provided the company performs appropriate supplier assessments and ensures that the system meets its intended use in the specific GMP environment.
Practical Impact of GAMP 5
GAMP 5 has become the reference point for regulators, auditors, and industry professionals. During inspections, authorities often assess CSV activities in line with GAMP 5 expectations, although this is not a legally binding requirement.
Companies that align their validation practices with GAMP 5 typically demonstrate greater control, efficiency, and consistency across their computerized systems.
Related Article: GAMP 5 Impact in CSV
CSV Lifecycle Process in GMP
The lifecycle approach is central to Computer System Validation. GAMP 5 provides the foundation, describing four main phases: Concept, Project, Operation, and Retirement.
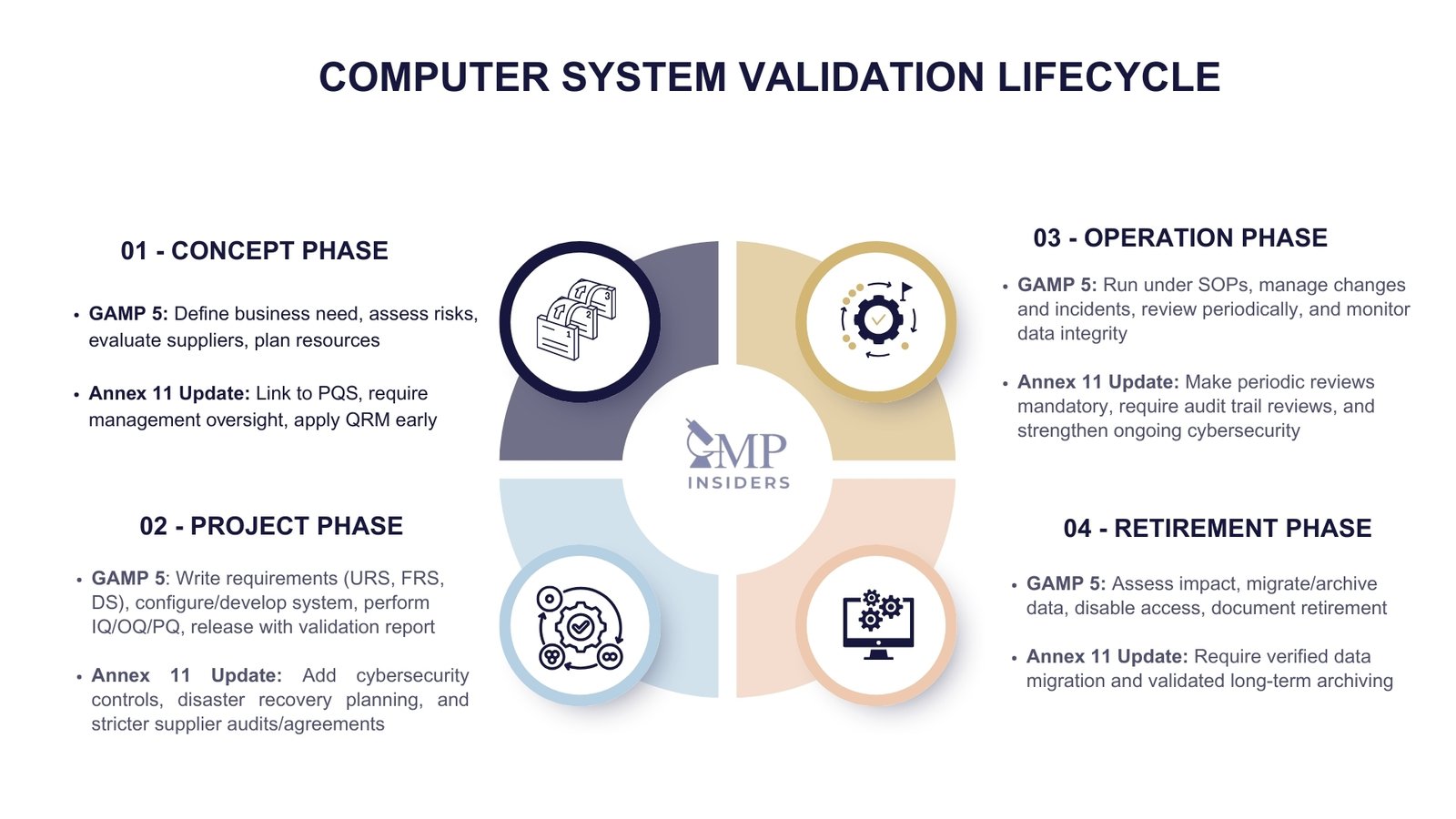
The draft revision of Annex 11 builds on this model, adding greater detail and binding expectations in areas such as risk management, cybersecurity, periodic reviews, and long-term data archiving.
1. Concept Phase
The concept phase establishes the foundation for validation by defining the business need and intended GMP use of the system. At this stage, companies evaluate whether a new system is required, explore potential solutions, and identify the key regulatory implications.
Typical activities include:
- Defining the scope and objectives of the system.
- Performing an initial high-level risk assessment to determine potential impacts on product quality, patient safety, and data integrity.
- Evaluating available suppliers and technologies (COTS vs. configurable vs. bespoke).
- Outlining preliminary budget, resource needs, and project timelines.
Annex 11 update: The draft revision makes clear that the concept phase must be explicitly integrated into the Pharmaceutical Quality System (PQS). Senior management is accountable for ensuring governance of computerized systems at this stage, with early application of Quality Risk Management (QRM) to guide the level of validation effort.
2. Project Phase
The project phase is the most intensive part of the lifecycle, where requirements are defined, the system is developed or configured, and validation activities are carried out.
Key elements of the project phase:
- Planning: Develop a project plan and, if applicable, a system-specific Validation Plan. Define responsibilities, deliverables, and timelines.
- Specification: Create structured documentation of requirements, starting with the User Requirement Specification (URS), followed by functional and design specifications. These must be testable, risk-based, and traceable.
- Configuration and Development: Configure or develop the system according to specifications, ensuring change management and version control are applied. Supplier involvement is critical here, as vendor testing and documentation can be leveraged.
- Verification and Testing: Conduct structured testing activities, which typically include Installation Qualification (IQ), Operational Qualification (OQ), and Performance Qualification (PQ). Testing must be risk-based, with focus placed on critical functions.
- Acceptance and Release: Summarize all activities in a Validation Report, confirm that acceptance criteria are met, and formally release the system for GMP use with Quality Assurance approval.
Annex 11 update: Stronger emphasis is placed on cybersecurity and business continuity controls during this phase.
Requirements now include patch management, antivirus protection, penetration testing, and disaster recovery planning (with defined recovery time and recovery point objectives). Supplier oversight is more prescriptive, requiring formal audits, quality agreements, and straightforward assignment of responsibilities between the company and the vendor.
3. Operation Phase
Once in use, the system must remain in a validated state for as long as it supports GMP activities. This requires ongoing monitoring, maintenance, and control.
Key activities include:
- Operating the system under approved SOPs to ensure consistency and compliance.
- Implementing change control for all system modifications, patches, and upgrades.
- Managing incidents, deviations, and corrective actions, with documentation of investigations.
- Performing periodic reviews to verify that the system remains compliant with current regulations and business needs.
- Reviewing audit trails, backup logs, and security reports to maintain data integrity.
- Ensuring continued supplier support, particularly for externally hosted or cloud-based systems.
Annex 11 update: The draft revision makes periodic reviews mandatory and provides detailed expectations for their scope, covering system performance, data integrity, cybersecurity measures, and supplier service quality.
Audit trail review is also strengthened: it is not sufficient for audit trails to exist; they must be routinely reviewed, assessed by trained personnel, and findings documented.
4. Retirement Phase
When a system is no longer required, it must be decommissioned in a controlled and documented manner. Retirement is not simply switching off the system but involves ensuring that data remains accessible for the required retention period.
Typical activities include:
- Performing an impact assessment to determine data retention and migration needs.
- Migrating GMP-relevant data into a new system or securely archiving it in a retrievable format.
- Disabling user access and deactivating system functions.
- Documenting the decommissioning process in a retirement report, including justification, activities performed, and records of data handling.
Annex 11 update: Retirement now carries more explicit requirements. Companies must ensure long-term archiving in a way that preserves data integrity and retrievability for the full retention period. When data is migrated to new systems, verification of the data migration is required to confirm its completeness and accuracy.
The V-Model in CSV
This lifecycle is often illustrated using the V-model, which maps specification activities on the left side of the “V” to corresponding verification activities on the right.
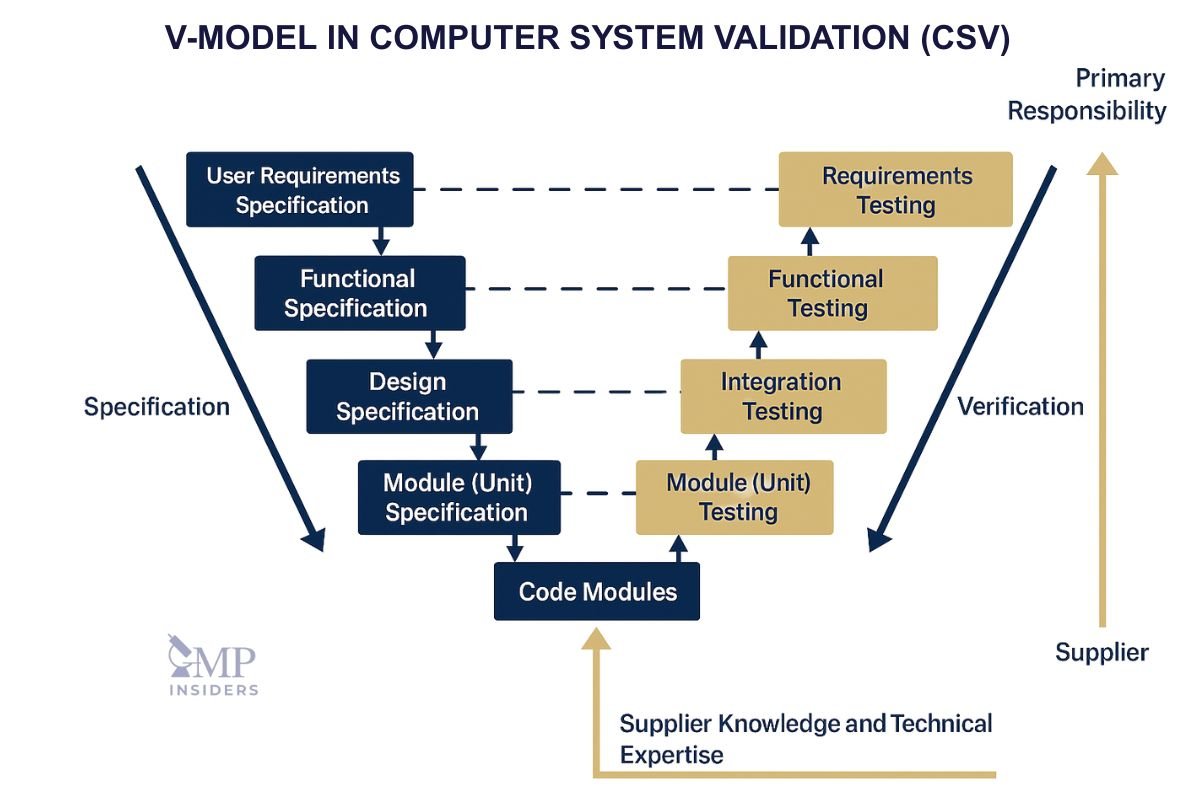
For example:
- URS (User Requirement Specification) ↔ PQ (Performance Qualification)
- FRS (Functional Requirement Specification) ↔ OQ (Operational Qualification)
- DS (Design Specification) ↔ IQ (Installation Qualification)
The V-model ensures complete traceability between requirements and testing, providing clear evidence that each defined need is systematically verified. Regulators and auditors often expect to see this model reflected in validation documentation, as it demonstrates a structured, risk-based approach to control over computerized systems.
Documentation in Computer System Validation
Documentation is one of the most scrutinized elements of Computer System Validation. It provides the objective evidence that the validation lifecycle has been planned, executed, and maintained in a manner consistent with GMP principles.
For regulators, well-prepared documentation demonstrates that a company has exercised control over its computerized systems; for the company, it provides confidence that the system will perform reliably in daily operation.
Key Documentation Components in CSV
The key documentation used in Computer System Validation includes:
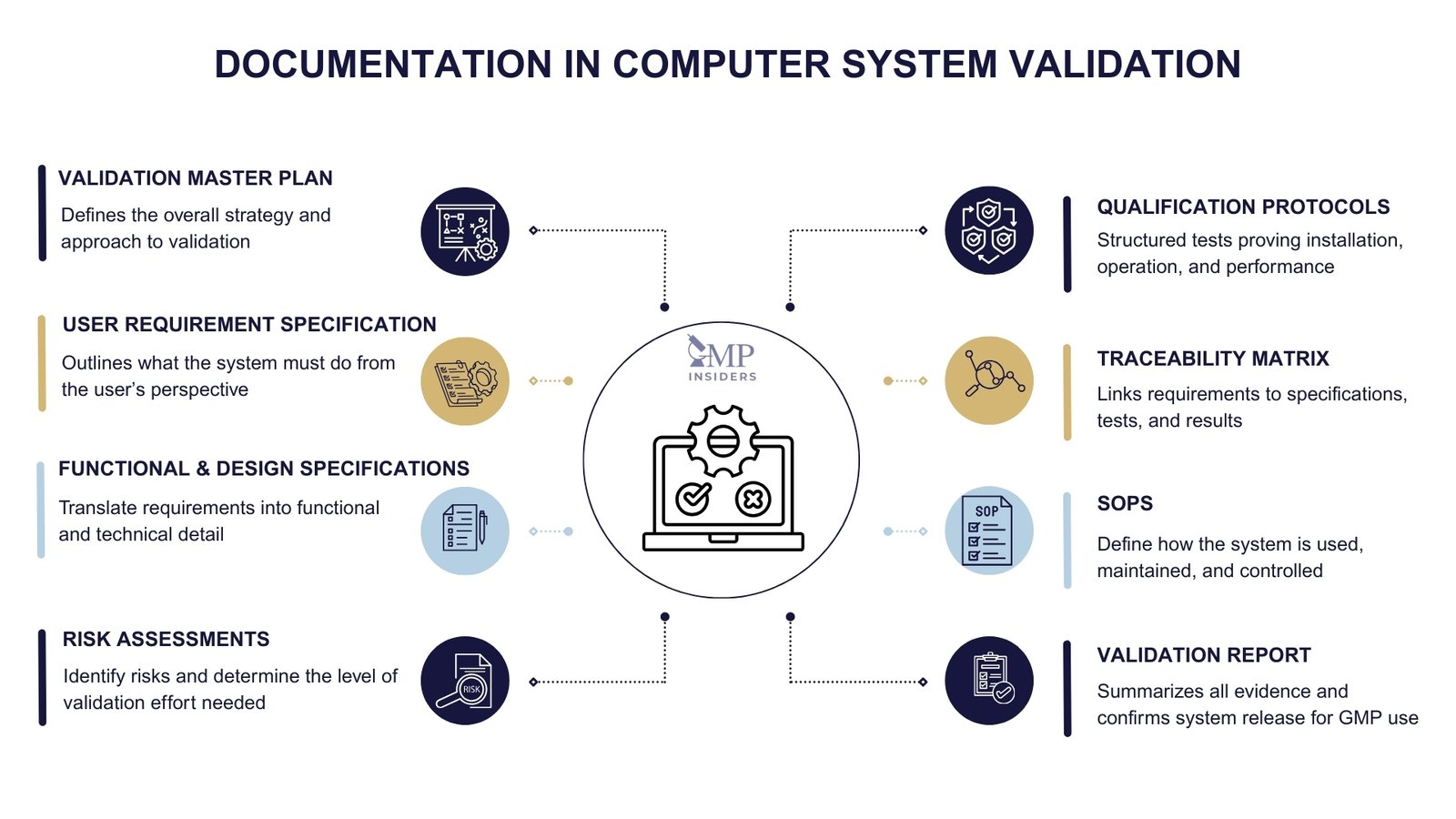
1. Validation Master Plan (VMP)
The VMP is a high-level document that describes the company’s overall approach to validation, including its policies, scope, responsibilities, and methodologies. In the context of CSV, the VMP establishes how computerized systems are selected, validated, and maintained in a validated state.
2. User Requirement Specification (URS)
The URS captures the intended purpose of the system from the user’s perspective. It defines what the system must be able to do, without describing how it will be achieved. A well-written URS is essential because it forms the basis for functional requirements and subsequent testing.
3. Functional and Design Specifications (FRS and DS)
The FRS translates user requirements into detailed functional expectations, while the DS describes how the system will be configured or developed to meet those requirements. These documents establish a bridge between user needs and technical implementation.
4. Risk Assessments
Risk assessments identify potential failures or weaknesses that could compromise product quality, patient safety, or data integrity. By applying principles from ICH Q9, companies can tailor the extent of validation effort to the level of risk.
For example, systems that directly generate batch release data require more extensive validation than those used for administrative purposes.
5. Qualification Protocols and Reports (IQ, OQ, PQ)
- Installation Qualification (IQ): Confirms that the system has been installed in accordance with the specified requirements.
- Operational Qualification (OQ): Verifies that the system operates correctly under defined conditions.
- Performance Qualification (PQ): Demonstrates that the system consistently performs as intended in its GMP environment.
Each qualification phase is executed according to a pre-approved protocol, with deviations documented and justified in the final report.
6. Traceability Matrix
The traceability matrix is a critical tool linking requirements from the URS to corresponding specifications, test cases, and qualification results. It ensures complete coverage, transparency, and accountability across the validation lifecycle.
7. Standard Operating Procedures (SOPs)
SOPs outline the procedures for using, maintaining, and controlling the system under GMP. These documents cover activities such as system operation, backup and recovery, change management, and incident handling. Without SOPs, validated systems cannot be operated in compliance with regulations.
8. Validation Report
The validation report consolidates all evidence generated throughout the lifecycle into a single, comprehensive summary document. It confirms whether the system has met its predefined requirements and whether it can be released for GMP use.
Ongoing Documentation Requirements
Validation documentation does not end once the system goes live. Regulators expect continuous evidence that the system remains validated throughout its operational life. This includes:
- Change control records for updates, patches, or modifications.
- Deviation and incident reports with documented investigations and corrective actions.
- Periodic review reports confirming ongoing compliance with regulations and internal procedures.
- Audit trail records generated by the system itself, demonstrating traceability of user actions and changes.
Annex 11 Updates to Documentation
The draft revision of EU GMP Annex 11 introduces new and more detailed requirements, expanding the scope of CSV documentation:
- Integration with PQS: Validation activities must be explicitly linked to the Pharmaceutical Quality System, with management oversight and governance documented.
- Cybersecurity and Business Continuity: Evidence of cybersecurity controls, penetration testing, patch management, and disaster recovery planning (RTO/RPO) must be documented.
- Periodic Reviews: Now a mandatory requirement, including structured documentation of data integrity checks, system performance, supplier services, and security measures.
- Audit Trail Reviews: Not only are they required to exist, but documented evidence of regular review by trained staff must also be maintained.
- Data Migration and Archiving: Verification of records of complete and accurate data transfer, and validation of long-term archiving solutions.
Emerging Trends: From CSV to CSA
For more than two decades, Computer System Validation (CSV) has been the standard approach for ensuring compliance of computerized systems in the pharmaceutical industry.
While effective in principle, CSV has often been criticized for becoming overly documentation-driven, with companies focusing more on generating evidence for inspectors than on assuring that systems are truly reliable and fit for use.
Recognizing these limitations, the U.S. FDA formalized Computer Software Assurance (CSA) in its 2025 guidance “Computer Software Assurance for Production and Quality System Software”, providing a modern, risk-based framework for system validation.
CSA does not replace CSV but reframes it, shifting the emphasis away from exhaustive paperwork and toward activities that add real value in terms of product quality and patient safety.
The main principles of CSA include:
Critical thinking first: validation activities should be guided by a clear understanding of how the system impacts GMP processes and patient safety.
Risk-based focus: high-risk functions that directly influence product quality or data integrity should receive the most rigorous testing and controls.
Efficient use of testing: scripted testing should be applied where it is most meaningful, while unscripted or exploratory testing can be used to gain broader system assurance.
Reduced documentation burden: evidence should be appropriate, but unnecessary repetition and excessive formal documentation should be avoided.
For the pharmaceutical industry, the move toward CSA represents a cultural change. Instead of treating validation as a regulatory checklist, companies are encouraged to view it as a process of building and maintaining confidence in computerized systems.
This aligns with broader industry trends such as digital transformation, cloud adoption, and the integration of advanced analytics into GMP environments.
While CSA is now established in FDA guidance, it has not yet been formally adopted in EU GMP. However, its principles are increasingly being discussed globally, and many organizations are beginning to harmonize their validation practices with CSA concepts to gain efficiency while maintaining compliance.
Related Article: CSV vs CSA in Software Validation
Regulatory Landscape for Computer System Validation
The regulatory framework for Computer System Validation (CSV) in the pharmaceutical industry is built on a combination of binding requirements and widely accepted guidelines. Each framework has its own scope and focus, but together they set clear expectations for ensuring that computerized systems are validated, reliable, and secure throughout their lifecycle.
FDA 21 CFR Part 11
In the United States, the Food and Drug Administration (FDA) defines requirements for electronic records and electronic signatures under 21 CFR Part 11. This regulation establishes the criteria by which electronic records are considered trustworthy, reliable, and equivalent to paper records.
Key requirements include:
- Validation of systems used to create, modify, maintain, or transmit electronic records.
- Secure and limited system access to authorized individuals.
- Generation of computer-generated audit trails that record operator actions.
- Use of electronic signatures that are unique, verifiable, and legally binding.
For pharmaceutical companies, Part 11 applies broadly across GMP-relevant systems, including laboratory instruments, manufacturing execution systems, and quality management platforms. Failure to comply often results in FDA Form 483 observations or warning letters during inspections.
EU GMP Annex 11
In Europe, Annex 11 of the EU Guidelines to Good Manufacturing Practice sets the expectations for computerized systems used in GMP-regulated activities.
Core requirements include:
- Documented validation of systems before use and throughout their lifecycle.
- Clear roles and responsibilities between system owners, QA, and IT.
- Emphasis on data integrity, including audit trails and access controls.
- Risk management principles applied to system design, operation, and change control.
- Supplier and service provider assessment to ensure quality is maintained across outsourced systems.
EU GMP Annex 11 (Draft Revision, 2025)
The draft revision of Annex 11 significantly expands expectations for computerized systems, growing from a concise 5-page document to a comprehensive guideline of 17 sections. The update reflects the realities of digitalization, cloud adoption, and cybersecurity challenges. Among the most notable enhancements are:
- Integration with the Pharmaceutical Quality System (PQS): CSV must be embedded in the company’s PQS, with senior management accountability.
- Expanded role of Quality Risk Management (QRM): Risk-based principles must be applied consistently across all lifecycle phases.
- Cybersecurity and business continuity: New requirements for firewalls, patch management, penetration testing, antivirus, and disaster recovery planning (including recovery time and recovery point objectives).
- Audit trails and electronic signatures: Greater detail on how audit trails must be configured, reviewed, and maintained, with expanded alignment to 21 CFR Part 11.
- Periodic reviews: Now mandatory, with defined expectations for assessing system performance, data integrity, security, and supplier performance.
- Data migration and archiving: Prescriptive requirements to ensure complete, accurate, and retrievable records during system replacement or retirement.
SEE ALSO: Annex 11 vs. 21 CFR Part 11: Comparison and Differences
ICH Q9: Quality Risk Management
While not specific to computerized systems, ICH Q9 provides the foundation for applying risk-based principles to CSV. Regulators expect that the extent of validation activities, documentation, and testing should be commensurate with the risk the system poses to product quality and patient safety.
For example, a laboratory instrument that directly generates release data for a batch requires more extensive validation than a system used for training records. By applying Q9 principles, companies can justify their level of validation effort and demonstrate that resources are focused where risks are greatest.
ISPE GAMP 5: Good Automated Manufacturing Practice
The GAMP 5 guide, published by ISPE, is not a regulation but a globally recognized good practice standard for implementing CSV. It provides a structured approach for categorizing systems, scaling validation activities, and managing the system lifecycle.
Key contributions of GAMP 5 include:
- A system categorization model (Categories 1–5) that helps determine validation effort based on system complexity.
- A lifecycle model covering concept, project, operation, and retirement phases.
- Emphasis on supplier involvement, leveraging vendor documentation where possible.
- Practical guidance on documentation, testing, and maintaining the validated state.
GAMP 5 is widely referenced during inspections and is considered the industry benchmark for CSV. Companies that align with GAMP 5 principles are generally better positioned to demonstrate compliance and withstand regulatory scrutiny.
Other Relevant Standards
Depending on the type of system, additional international standards may apply. For example:
- ISO 13485 for quality management systems in medical device manufacturing, relevant when systems are used in both pharma and device contexts.
- ISO 27001 for information security management, important when computerized systems handle large volumes of sensitive or patient-related data.
While these standards are not mandatory under GMP, they provide valuable frameworks that support compliance and data protection objectives in highly regulated environments.
FAQ
What Is the Difference Between CSV and Software Testing?
Software testing focuses only on verifying functionality against specifications, while CSV encompasses the entire lifecycle of a computerized system. CSV covers planning, specifications, qualification, operation, and retirement, ensuring regulatory compliance and data integrity. It is therefore broader and more formalized than traditional software testing.
When Does a Computerized System Need to Be Validated?
Any system that directly or indirectly impacts GMP processes, product quality, patient safety, or data integrity must be validated before use. Validation should occur prior to GMP operation and be maintained throughout the system’s lifecycle. This includes periodic reviews and re-validation after significant changes.
Does Cloud-Based Software Require Validation?
Yes, cloud-based systems used in GMP environments require validation just like on-premises systems. The company remains responsible for ensuring compliance, even if a third-party provider manages the infrastructure. Supplier assessment and quality agreements are critical when using Software as a Service (SaaS) platforms.
What Is the Role of Audit Trails in CSV?
Audit trails record who did what and when within a computerized system, creating transparency and accountability. They are critical for data integrity because they prevent undetected changes to GMP records. Regulators expect audit trails to be secure, time-stamped, and reviewed regularly.
How Does CSV Relate to Data Integrity?
CSV assures that computerized systems manage GMP data reliably and consistently. By validating system controls such as audit trails, user access, and backup processes, companies reduce the risk of data manipulation or loss. Data integrity is therefore both a core objective and outcome of CSV.
How Often Should a Validated System Be Reviewed?
Validated systems should undergo periodic reviews to confirm they remain compliant and fit for purpose. The frequency depends on system complexity, criticality, and regulatory requirements; however, annual reviews are a common practice. These reviews should assess performance, change history, and any new risks that have arisen.
What Is Computer System Decommissioning?
Decommissioning is the controlled retirement of a computerized system that is no longer in use. It involves securing or migrating GMP data, disabling access rights, and documenting the process to maintain regulatory compliance. Inspectors often review decommissioning records to ensure data integrity is preserved.
How Are System Upgrades Handled in CSV?
Upgrades must undergo a formal change control process to assess their potential impact on validation status. Depending on the scope, re-validation or partial qualification may be required. Documentation of the change, testing, and approval is essential to maintain compliance.
Conclusion
Computer System Validation remains a fundamental element of Good Manufacturing Practice, assuring that computerized systems used in pharmaceutical environments are reliable, compliant, and capable of protecting patient safety.
By following a lifecycle approach supported by regulatory frameworks such as FDA 21 CFR Part 11, EU GMP Annex 11, ICH Q9, and industry guidance like GAMP 5, companies can demonstrate control over systems that manage critical GMP processes and data.
The challenges of CSV often lie not in regulatory expectations but in execution. Excessive documentation, inconsistent application of risk principles, weak supplier oversight, and insufficient controls for data integrity are common findings during inspections. Addressing these issues requires a structured, pragmatic approach that balances compliance with efficiency.
As digital transformation accelerates and the industry moves toward risk-based models such as Computer Software Assurance, CSV will continue to evolve. What remains unchanged is its central purpose: ensuring that pharmaceutical companies can rely on computerized systems to deliver accurate, consistent, and trustworthy outcomes in support of high-quality medicines.