Pharmaceutical operations rely on increasingly complex digital infrastructures. Laboratory platforms generate high volumes of analytical data, manufacturing execution systems manage critical process parameters in real-time, and electronic quality systems drive decision-making throughout the product lifecycle.
Each of these systems must not only function reliably but also withstand regulatory scrutiny regarding data integrity and patient safety.
Software validation provides the framework to achieve this assurance. It applies structured, documented activities to confirm that systems operate as intended, from initial specification through continuous use. Guidance documents, such as FDA 21 CFR Part 11, EU GMP Annex 11, and GAMP 5, establish expectations for lifecycle management and risk-based validation strategies.
Yet the speed of system updates, cloud adoption, and agile deployment models challenge traditional validation practices. This has brought increasing focus on continuous software validation, where assurance is embedded into system operations and maintained dynamically rather than through static, periodic efforts.
In this article, we examine the role of software validation in the pharmaceutical industry, the regulatory framework that defines it, and the lifecycle principles that guide its implementation. We also explore how continuous software validation is reshaping compliance strategies, enabling organizations to sustain validated states while adapting to digital transformation.
What is Software Validation?
Software validation is the documented process of ensuring that a computerized system performs its intended functions consistently, accurately, and in compliance with regulatory requirements. In the pharmaceutical industry, validation applies to systems that directly or indirectly affect product quality, patient safety, or data integrity.
The concept extends beyond a one-time qualification. It encompasses the entire lifecycle of a system, from defining user requirements and specifications, through development and testing, to operational use and eventual retirement. At each stage, evidence must demonstrate that the system remains fit for purpose.
“Confirmation by examination and provision of objective evidence that software specifications conform to user needs and intended uses, and that the particular requirements implemented through software can be consistently fulfilled.”
Key Objectives of Software Validation in GxP Environments
The objectives of software validation can be grouped into several core areas, each addressing a critical aspect of compliance and system reliability:
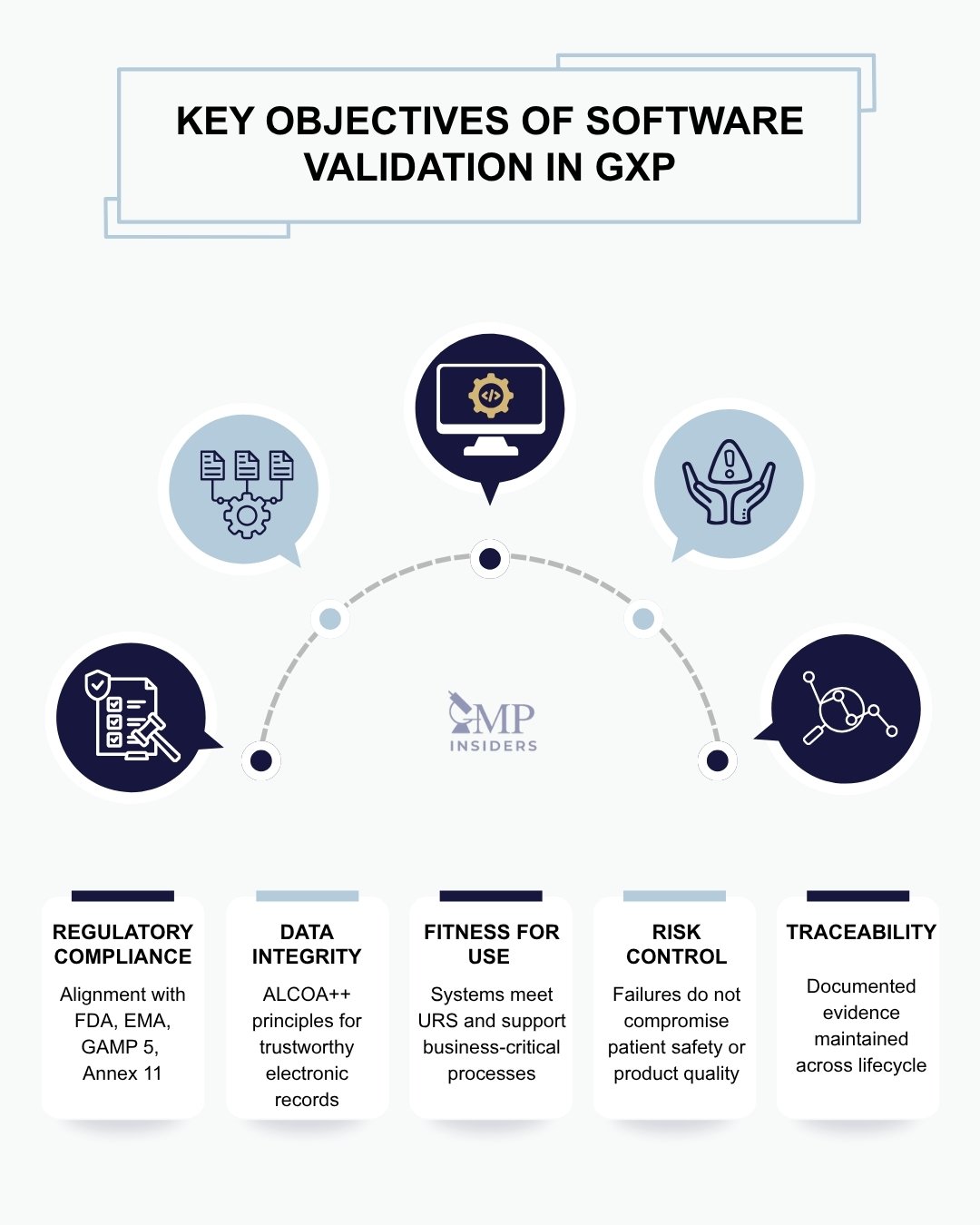
- Regulatory compliance: Demonstrating alignment with FDA, EMA, GAMP 5 and other authority expectations.
- Data integrity: Guaranteeing compliance with ALCOA++ principles for trustworthy electronic records.
- Fitness for use: Confirming that systems meet user requirements and support critical business processes.
- Risk control: Ensuring that system failures do not compromise patient safety or product quality.
- Traceability: Providing documented evidence across the entire system lifecycle.
Software Validation vs. Software Verification
The terms “validation” and “verification” are related but distinct concepts in GxP compliance. Both are essential, but they address different questions about computerized systems.
- Software Verification asks: “Did we build the system right?”
- Focuses on confirming that the system or component meets its specified requirements.
- Typically involves design reviews, code checks, and functional testing.
- Answers whether the system has been developed according to the defined specifications.
- Software Validation asks: “Did we build the right system?”
- Focuses on ensuring that the system fulfills its intended use in the operational environment.
- Demonstrates that the system, as implemented, supports GxP processes reliably and complies with regulatory requirements.
- Provides documented evidence that the system consistently performs as intended throughout its lifecycle.
In practical terms:
- Verification is about compliance with specifications.
- Validation is about compliance with intended use under real conditions.
Both activities complement one another. Verification ensures accuracy during development, while validation ensures fitness for purpose in a regulated environment. Together, they provide the assurance needed to satisfy regulators that systems are trustworthy, reliable, and suitable for GxP operations.
Related Article: Software Validation vs Verification in GMP
General Principles of Software Validation
Software validation in the pharmaceutical industry is not a single activity but a framework built on interconnected principles. These general principles guide the specification, testing, and maintenance of systems throughout their lifecycle, ensuring that compliance is sustained even as technology evolves.
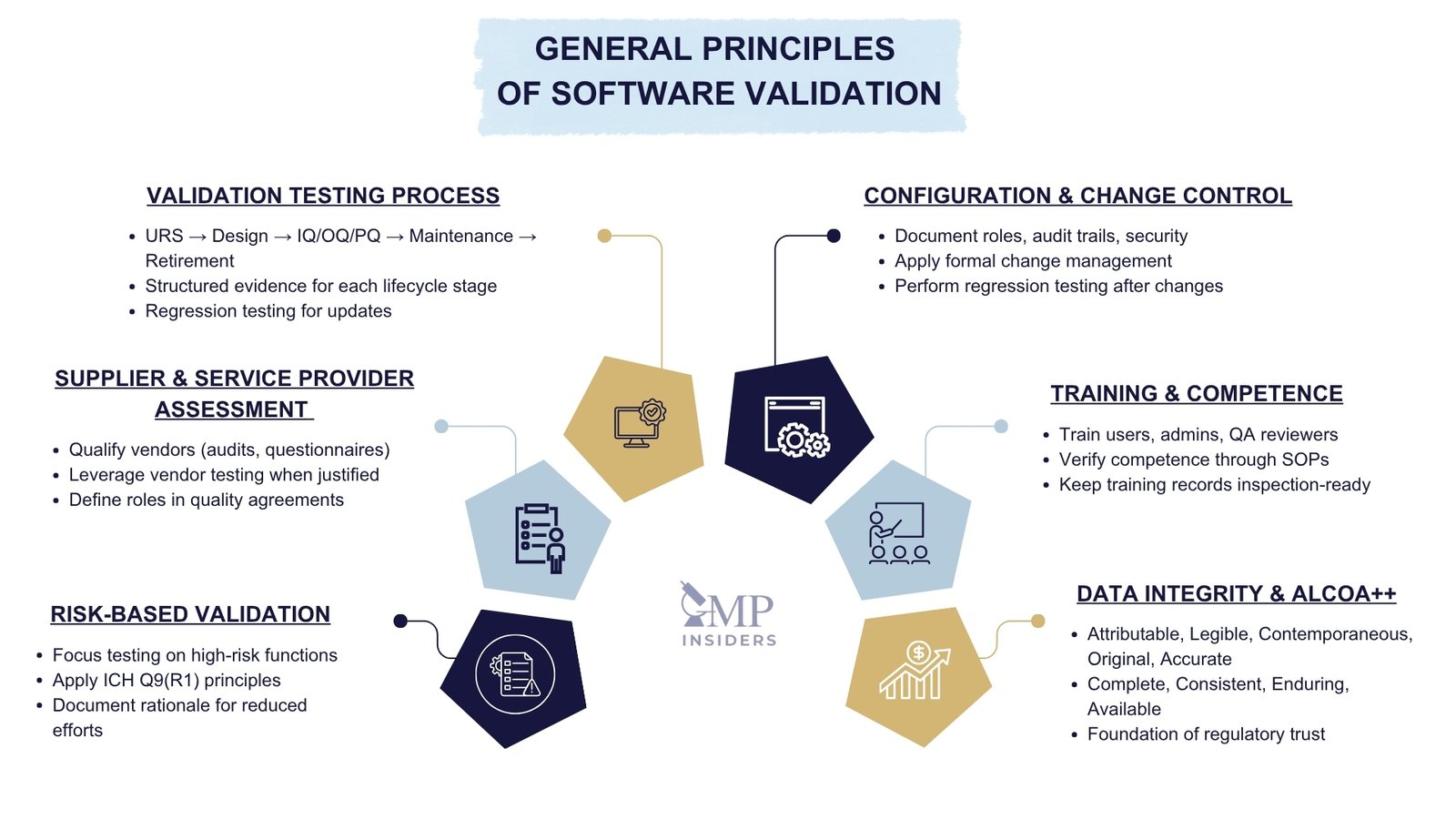
Risk-Based Validation of Software
Not all systems or functions carry the same level of regulatory impact. A risk-based approach ensures that validation efforts are proportionate to the potential consequences of system failure. By aligning with ICH Q9(R1) principles, organizations can focus resources where risks to patient safety, product quality, or data integrity are highest.
Typical considerations include:
- Assessing the system’s role in critical GxP processes.
- Prioritizing testing for high-risk functionalities.
- Documenting rationale for reduced testing of low-risk features.
Supplier and Service Provider Assessment
Most computerized systems are supplied, configured, or maintained by external vendors. Regulators expect companies to demonstrate oversight and qualification of these suppliers. Key elements include:
- Conducting vendor audits, questionnaires, or reviews.
- Leveraging vendor documentation where appropriate (per GAMP 5).
- Establishing quality agreements that define roles and responsibilities.
This principle ensures that reliance on third-party systems does not introduce hidden compliance risks.
Software Validation Testing Process
Software validation is a structured process that spans the entire lifecycle of a computerized system. Each stage generates documented evidence to demonstrate that the system remains fit for its intended use, compliant with regulations, and reliable in protecting product quality and patient safety.
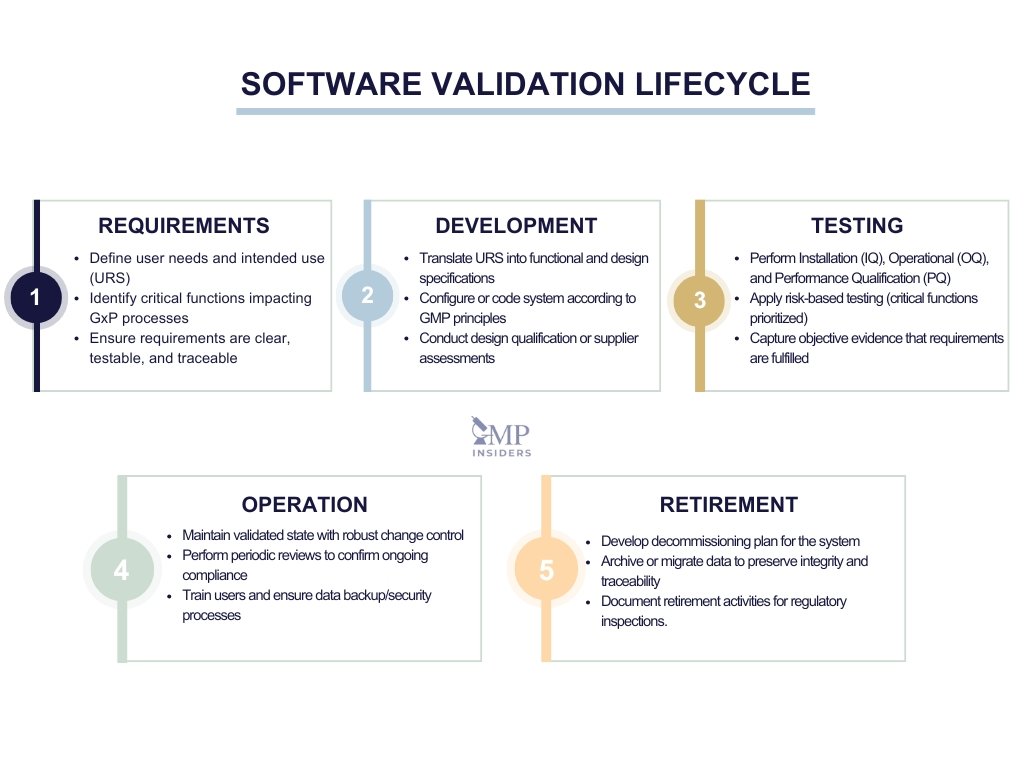
Requirements
The process begins with the definition of user and regulatory needs, captured in the User Requirements Specification (URS). This stage establishes the foundation for all subsequent validation activities.
A strong URS ensures that system functions are aligned with business processes and regulatory expectations, while also providing the framework for testing and traceability. Poorly written or vague requirements are a frequent source of inspection findings because they create gaps in coverage later in the lifecycle.
- Define user needs and intended use in a clear, unambiguous URS
- Identify and prioritize critical functions that directly impact GxP compliance
- Ensure requirements are testable, traceable, and risk-ranked for validation focus
Design and Development
This stage translates the URS into detailed functional and technical specifications. For custom-built systems, this may involve software coding and design reviews. For commercial off-the-shelf (COTS) or configurable systems, it involves documenting supplier specifications and configuration choices.
Design qualification activities ensure that the system design is capable of meeting intended use and aligns with GMP principles before testing begins.
Testing (IQ, OQ, PQ)
Testing provides documented evidence that the system works as intended. It is structured into three qualification phases:
- Installation Qualification (IQ) – confirms correct installation, version control, and configuration of hardware and software.
- Operational Qualification (OQ) – verifies that functions perform as expected under controlled conditions, often based on risk assessment.
- Performance Qualification (PQ) – demonstrates consistent performance under real-world operating conditions in the user environment.
In addition, regression testing may be required to confirm that updates, patches, or changes do not negatively impact validated functions.
See Also: Importance of IQ, OQ and PQ in GMP
Operational Maintenance
Once in routine use, systems must remain in a validated state. This requires robust change control to assess the impact of updates or configuration changes, and periodic reviews to confirm continued compliance with regulatory expectations.
Supporting processes such as training, incident management, and data backup also form part of maintaining validation. Neglecting this stage is a frequent cause of systems drifting out of compliance.
Retirement
At the end of a system’s lifecycle, validation does not simply stop. Retirement activities ensure that data and records are securely archived, remain accessible for the full retention period, and preserve traceability for inspections.
A retirement plan should document how the system will be decommissioned, how historical data will be migrated or stored, and how compliance will be demonstrated if legacy records are requested.
Configuration and Change Control
Validation is not a one-time activity. Systems must remain validated as they evolve. Key activities include:
- Documenting system configurations such as user roles, audit trails, and security parameters.
- Managing patches, upgrades, and parameter changes under formal change control.
- Performing regression testing where changes may impact validated functions.
This principle prevents systems from “drifting” out of compliance over time.
Related Article: Change Control in Pharma
Training and Competence
Even the best-validated system cannot ensure compliance if users lack the knowledge to operate it correctly. Essential components include:
- Training for end users, administrators, and QA reviewers.
- Competency assessments tied to role-specific SOPs.
- Documented training records available for inspection.
Trained personnel ensure that validation is consistently applied in practice, not just on paper.
Data Integrity and ALCOA++
At the core of every validation effort lies data integrity. Electronic records must remain trustworthy throughout the product lifecycle, meeting the ALCOA++ principles.
Embedding these principles into validation ensures that system outputs are both technically sound and compliant with regulatory expectations. This creates confidence that data supporting batch release, stability studies, or regulatory submissions is reliable and defensible during inspections.
See Also: Data Integrity and Data Governance in GMP
Software Validation Documentation
Beyond testing activities, software validation in the pharmaceutical industry is executed through a structured process. This process ensures that all validation activities are controlled, traceable, and aligned with regulatory expectations.
| Document | Purpose | Key Elements |
|---|---|---|
| URS (User Requirement Specification) | Defines intended use and requirements of the system. | Functional & non-functional needs, compliance expectations, access levels. |
| RTM (Requirements Traceability Matrix) | Ensures every requirement is covered and verified. | Requirement ID, linked specs, test cases, results, evidence references. |
| Validation Plan | Outlines overall strategy and scope of validation. | Purpose, scope, risk-based testing, roles, deliverables, acceptance criteria. |
| Validation Protocol | Provides step-by-step execution instructions for testing. | Test cases, test data, pass/fail criteria, deviation handling, approvals. |
| Validation Summary Report (VSR) | Closes the loop, documenting final validated state of the system. | Test outcomes, traceability, deviations, conclusion, final approvals. |
User Requirement Specification (URS)
The URS is the foundation of the software validation process. It defines what the system is expected to do, serving as the benchmark against which all subsequent validation activities are measured. A well-written URS is clear, testable, and directly aligned with the intended use of the system in a GxP environment. Typical elements include:
- Functional requirements (system capabilities, data handling, reporting).
- Non-functional requirements (performance, security, reliability).
- Regulatory and compliance expectations (e.g., 21 CFR Part 11, Annex 11).
- Interfaces with other systems or equipment.
- User access levels and permissions.
- Data integrity and audit trail requirements.
The URS provides the traceability framework for validation by linking requirements to design, test cases, and final reports. Its clarity and completeness are essential to demonstrating that the validated system meets both business needs and regulatory expectations.
Requirements Traceability Matrix (RTM)
The RTM is the backbone of validation evidence. It establishes a direct link between user requirements, specifications, test cases, and results. Its purpose is to demonstrate complete coverage and prove that nothing was overlooked during the validation process. Typical elements include:
- Requirement ID – references the URS or regulatory requirement.
- Linked Specification – FS/DS section that describes how the requirement is implemented.
- Test Case ID – protocol step that verifies the requirement.
- Result/Status – outcome of the executed test (pass/fail, with deviations noted).
- Reference to Evidence – location of raw data, screenshots, or signed test records.
By maintaining this one-to-one mapping, the RTM provides inspectors with a transparent and defendable record that all critical requirements were verified and met. It also serves as a living document, updated during change control, to ensure the validated state of the system is preserved throughout its lifecycle.
Software Validation Plan
The plan is the blueprint of the validation project. It defines the overall strategy, scope, and responsibilities before any testing begins. Typical contents include:
- Purpose and scope of validation.
- System description and intended use.
- Risk-based strategy for testing.
- Roles and responsibilities (QA, IT, system owner, supplier).
- List of deliverables (URS, test cases, reports).
- Acceptance criteria for system release.
The plan provides regulators and stakeholders with a clear view of how validation will be carried out and controlled.
Software Validation Protocol
The protocol is the execution manual for validation. It translates the strategy defined in the plan into detailed, actionable steps. Typical contents include:
- Specific test cases linked to requirements.
- Test data and expected outcomes.
- Pass/fail criteria for each test.
- Instructions for documenting results.
- Procedures for handling deviations and unexpected results.
- Requirements for evidence collection and approvals.
Where the plan defines the “what” and “why,” the protocol defines the “how.” Together, they ensure that validation is reproducible, defendable, and inspection-ready.
Software Validation Summary Report (VSR)
The report is the final document that closes the validation loop. It summarizes the activities performed, results obtained, and conclusions reached. Key elements include:
- Summary of executed tests and outcomes.
- Traceability back to user requirements.
- Documentation of deviations and their resolutions.
- Assessment of whether acceptance criteria were met.
- Final conclusion on the validated state of the system.
- Approvals from QA, IT, and system owners.
The report provides the documented evidence that the system was validated according to the approved plan and protocol, creating a defensible record for regulatory inspections.
Continuous Software Validation
Traditional software validation models were developed for environments where systems changed slowly. Validation was often approached as a large-scale project during system implementation, followed by periodic revalidation when significant changes occurred.
This approach can create long gaps between assurance activities, during which systems may drift from a validated state, especially when frequent updates, patches, or configuration changes are introduced.
In today’s pharmaceutical landscape, systems evolve rapidly. Laboratory platforms are continually updated with new analytical methods, cloud providers release software patches on a weekly basis, and agile development cycles introduce features continuously. Under these conditions, the static model of validation introduces compliance risks and operational delays.
Continuous software validation addresses these challenges by integrating validation into daily operations. Instead of validation being a discrete event, it becomes a continuous process supported by automation, monitoring, and traceability. The goal is to maintain a validated state at all times, regardless of how frequently systems are updated or modified.
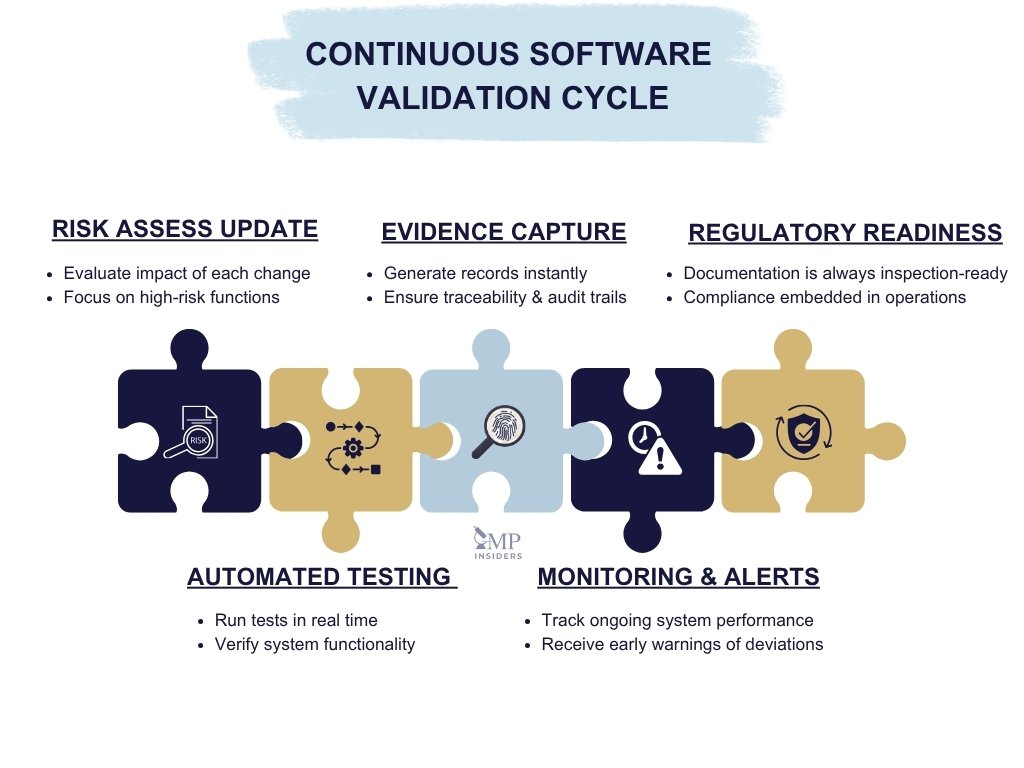
What Continuous Software Validation Means
Continuous validation is not a new regulatory requirement but a modern interpretation of existing lifecycle expectations. It applies the same principles of specification, risk assessment, testing, and documentation, only executed dynamically and in real time.
In practice, continuous validation ensures that:
- Each software update is risk-assessed and validated automatically where possible.
- Test evidence is generated and stored in real time, keeping systems inspection-ready.
- Ongoing monitoring confirms that the system continues to perform as intended.
- Compliance is achieved without interrupting business processes or delaying critical updates.
Benefits of Continuous Software Validation
For GxP-regulated companies, the move to continuous validation provides clear operational and compliance benefits:
- Reduced compliance risk: Real-time checks identify issues before they impact product quality or data integrity.
- Faster deployment: Updates and patches can be implemented without waiting for lengthy re-validation cycles.
- Resource efficiency: Automated testing and evidence generation reduce reliance on manual execution and documentation.
- Inspection readiness: Regulators can be presented with complete, traceable evidence at any point in the system lifecycle.
- Scalability: Continuous validation adapts to cloud environments and SaaS models, where frequent vendor-driven changes are the norm.
Challenges and Considerations
The adoption of continuous validation is not without hurdles. Organizations must carefully address both technical and regulatory aspects:
- Regulatory acceptance: Continuous validation must still align with the expectations of the FDA, EMA, and other regulatory authorities, ensuring that risk-based testing and documentation standards are not compromised.
- Infrastructure requirements: Automated testing and monitoring rely on strong IT foundations, including version control, audit trails, and integration with quality management systems.
- Change management: SOPs, validation master plans, and quality procedures may need to be rewritten to reflect continuous practices.
- Cultural shift: Quality and IT teams must move from project-based validation mindsets to ongoing, collaborative assurance models.
Traditional CSV vs Continuous Software Validation
Both traditional Computer System Validation (CSV) and continuous software validation share the same regulatory foundation, but the way they are executed differs significantly.
Traditional CSV relies on project-based validation events, often creating delays when systems change. Continuous validation, by contrast, integrates assurance into daily operations, using automation and monitoring to keep systems in a validated state at all times.
The table below highlights the main differences:
| Aspect | Traditional CSV | Continuous Software Validation |
|---|---|---|
| Approach | Project-based, executed at implementation and major changes | Embedded into daily operations with ongoing assurance |
| Testing | Manual, document-heavy IQ/OQ/PQ cycles | Automated, risk-based, and often integrated into CI/CD pipelines |
| Documentation | Large volumes of static documents prepared for audits | Dynamic, real-time evidence with full traceability |
| Regulatory alignment | Fully compliant but prone to over-documentation | Supports FDA CSA draft, Annex 11 draft, and GAMP 5 (2022) focus on critical thinking |
| System updates | Trigger re-validation projects and potential delays | Validated continuously, enabling faster adoption of patches and upgrades |
| Risk management | Applied mainly at project start and during re-validation | Integrated continuously, focused on high-risk functions |
| Resource use | High upfront effort, often repetitive | Optimized through automation and supplier testing |
| Inspection readiness | Evidence generated primarily for audits | Inspection-ready at all times through continuous traceability |
Related Article: Computer System Validation in Pharmaceutical Industry
Best Practices for Software Validation in GMP
Effective software validation depends on applying regulatory requirements in a structured and pragmatic way. Beyond initial implementation, organizations must maintain control of computerized systems throughout their lifecycle to ensure they remain reliable and inspection-ready.
The following practices form the foundation of compliant and efficient validation in GxP environments.
Documentation and Traceability
Validation must always be supported by clear, traceable documentation. Each activity should produce evidence that can be linked back to user requirements and risk assessments. A robust documentation package typically includes:
- Validation Master Plan (VMP) – Defines the overall validation strategy, scope, responsibilities, and approach to maintaining compliance across the system lifecycle.
- User Requirements Specification (URS) – States what the system is expected to do, forming the basis for design, testing, and traceability.
- Functional and Design Specifications (FS/DS) – Describe how requirements will be technically implemented, providing the blueprint against which testing is performed.
- Test Plans and Test Scripts – Detail how each requirement will be verified, including test cases, expected results, and pass/fail criteria.
- Validation Reports – Summarize executed activities, test outcomes, deviations and their resolutions, and provide a documented conclusion on whether acceptance criteria were met. These reports also capture the formal approval of the validated state by QA, IT, and the system owner.
Maintaining full traceability between requirements, risks, and test outcomes is critical to demonstrating compliance during inspections.
Testing Strategies
Testing verifies that systems function as intended and that controls effectively mitigate risks. A risk-based testing strategy strikes a balance between efficiency and compliance. Key testing phases—such as Installation Qualification (IQ), Operational Qualification (OQ), and Performance Qualification (PQ)—form the backbone of validation, but their detailed application is discussed in another section of this article.
In modern environments, automated testing tools can support regression testing, reducing the burden of re-executing manual scripts during updates.
Leveraging Automation and Digital Tools
Automation enhances both efficiency and consistency in validation activities. Examples include:
- Automated evidence capture – generating audit-ready logs without manual intervention.
- Continuous Integration/Continuous Deployment (CI/CD) – integrating validation testing into development pipelines for agile and SaaS systems.
- Automated Document Generation – Producing validation documents (e.g., protocols, reports, traceability matrices) directly from requirements and test management systems, with version control to prevent errors.
- Digital Traceability Tools – Linking URS, risks, test cases, and results in automated matrices that update dynamically as changes occur.
- Supplier testing leverage – using vendor documentation and certifications as part of the validation package, provided it is assessed and verified.
Maintaining Compliance Over Time
Validation is not complete at system release. Ongoing activities are essential to sustain the validated state:
- Periodic reviews – confirming that systems remain compliant with current regulatory and business requirements.
- Change control – assessing the impact of updates, patches, or configuration changes on validation status.
- Re-validation triggers – initiating additional testing when risks to compliance or functionality are identified.
- Training and SOP alignment – ensuring personnel understand how to operate and maintain validated systems correctly.
Regulatory Guidance for Computer Software Validation
The foundation of software validation in the pharmaceutical industry is defined by regulatory authorities and harmonized through international guidance documents. These references establish not only the requirement to validate computerized systems but also the expectations for how validation should be planned, executed, and maintained.
FDA Guidance: 21 CFR Part 11 and Computer Software Assurance (CSA)
The FDA requires that electronic records and signatures be trustworthy, reliable, and equivalent to paper records. Under 21 CFR Part 11, companies must validate any software that processes GxP data. More recently, the FDA has promoted Computer Software Assurance (CSA), issuing a guidance that encourages risk-based and critical-thinking approaches.
Key points include:
- Validation of systems impacting product quality, data integrity, or patient safety.
- Risk-based testing focused on high-impact functions.
- Use of supplier testing and automation where appropriate.
- Reduction of “checklist-style” documentation in favor of evidence that demonstrates actual assurance.
Related Article: Key differences between CSV and CSA in Software Validation
EU: Annex 11 and Annex 15
In Europe, computerized system validation is guided by Annex 11 and Annex 15 of the EU GMP Guide.
- Annex 11 (current version) requires validation of all systems used in GMP activities, with emphasis on data integrity, security, audit trails, and periodic review.
- Draft Annex 11 (2025 update) strengthens expectations by highlighting:
- Data integrity and ALCOA++ principles embedded into all system activities.
- Stronger oversight of third-party service providers, including cloud vendors.
- Risk-based approaches supported by documented rationales.
- Critical thinking in applying validation principles, moving away from excessive paperwork.
- Integration of continuous monitoring and assurance into lifecycle management.
- Annex 15 complements Annex 11 by describing general qualification and validation requirements across the product lifecycle, covering planning, testing, and ongoing maintenance.
GAMP 5 (Second Edition, 2022 Update)
The GAMP 5 framework, maintained by ISPE, remains the industry’s reference point for practical implementation. The Second Edition highlights:
- Applying risk-based approaches consistent with ICH Q9(R1).
- Encouraging critical thinking to avoid over-documentation.
- Leveraging supplier activities (e.g., vendor testing, certifications) where justified.
- Guidance for cloud, SaaS, and AI-enabled systems.
- Emphasis on continuous assurance, aligning with agile and DevOps methodologies.
Related Article: Impact of GAMP 5 in CSV
The Future of Software Validation in GxP
Software validation in the pharmaceutical industry is shifting from static, document-heavy projects to dynamic, risk-based assurance models. This transformation is driven by the need to keep pace with agile development, cloud adoption, and the rapid evolution of digital infrastructures.
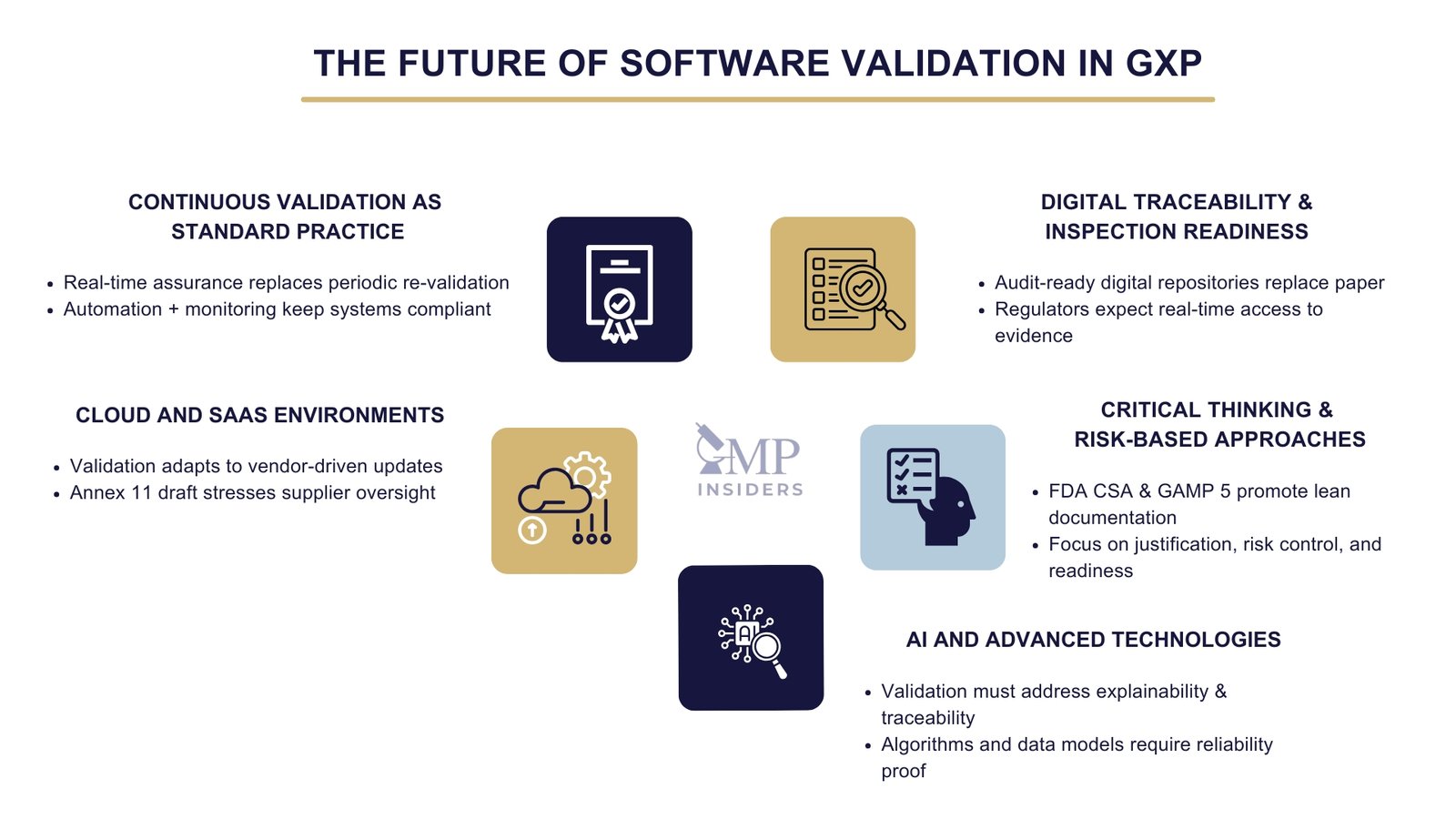
Continuous Validation as Standard Practice
The future direction of validation is continuous. Regulators are increasingly recognizing that maintaining a validated state requires embedded assurance rather than periodic re-validation. Automation, monitoring, and real-time evidence generation are becoming essential tools for sustaining compliance without interrupting business operations.
Cloud and SaaS Environments
As organizations migrate critical systems to the cloud, validation practices must adapt. Draft Annex 11 emphasizes the oversight of third-party providers, requiring companies to demonstrate that vendor testing and controls are integrated into their validation packages.
Continuous assurance is vital in SaaS environments, where frequent vendor-driven updates occur outside the company’s direct control.
AI and Advanced Technologies
Artificial intelligence, machine learning, and advanced analytics are gradually entering GxP environments. Validation of such systems presents new challenges, particularly in terms of explainability and traceability. Future guidance will likely require companies to demonstrate not only system functionality but also the reliability of their algorithms and data models.
Critical Thinking and Risk-Based Approaches
The evolution of regulatory expectations is clear: validation should be lean, focused, and risk-based. The FDA’s CSA draft, the EU Annex 11 draft, and GAMP 5 Second Edition all promote critical thinking over exhaustive documentation.
The emphasis is on justifying the chosen approach, demonstrating that risks are understood and controlled, and maintaining inspection readiness at all times.
Related Article: Quality Risk Management in CSV
Digital Traceability and Inspection Readiness
Digital, audit-ready repositories are increasingly replacing paper-heavy validation reports. Future inspection models will expect real-time access to validation evidence, enabling regulators to review system status at any point in the lifecycle. This shift reduces administrative burden while increasing transparency.
FAQ
Can Cloud-Hosted Systems Be Validated Under GxP Requirements?
Yes, cloud-hosted systems can be validated provided that risks are identified and mitigated. This includes ensuring contractual agreements with vendors cover responsibilities for data integrity, access control, and audit trails. Continuous monitoring is often necessary due to frequent updates beyond the company’s direct control.
Draft Annex 11 and GAMP 5 both provide guidance on validation strategies for cloud environments.
How Often Should Validated Software Be Reviewed?
Validated systems should undergo periodic reviews at intervals defined by the company’s procedures, typically every one to three years. The review ensures that the system remains compliant with current regulatory requirements and continues to meet its intended use.
Reviews should also confirm that updates, patches, and configuration changes have been adequately assessed through change control. Evidence of periodic review is a common focus point in inspections.
What Triggers the Need for Software Re-Validation?
Re-validation is required when significant changes occur that may impact system performance or compliance. Examples include major software upgrades, changes to system configuration, or integration with new platforms.
Risk assessments help determine whether full or partial re-validation is necessary. Minor patches or cosmetic updates may not require extensive re-validation if justified and documented.
What Is the Role of URS in Software Validation?
User Requirements Specifications (URS) form the foundation of software validation. They define what the system must do from the end user’s perspective and ensure alignment with business and regulatory needs.
Every test and validation activity must trace back to a specific requirement in the URS. Inadequate or vague requirements often lead to validation gaps and inspection findings.
Why Must COTS Software Be Validated if It Is Widely Used?
Even if COTS software is widely deployed, its intended use may differ across organizations. Regulators require evidence that the specific installation, configuration, and use case in your environment meet GxP expectations. Vendor testing or certifications may be leveraged, but are never sufficient on their own.
How Does Continuous Software Validation Apply to LIMS?
Continuous validation is especially relevant for Laboratory Information Management Systems (LIMS) because laboratories often apply updates, patches, or configuration changes to improve performance or meet new regulatory expectations. Embedding automated testing and monitoring into daily operations ensures that the LIMS remains validated even as it evolves.
This reduces downtime associated with re-validation projects and maintains inspection readiness. Continuous validation aligns with modern regulatory expectations for dynamic assurance of system compliance.
Why is Software Validation Critical for Medical Devices?
Unlike general GxP systems, medical device software often has a direct impact on patient safety. A malfunction could result in misdiagnosis, treatment errors, or device failures.
Validation provides assurance that risks have been identified and controlled, and that the system performs consistently under intended conditions. Regulators require manufacturers to demonstrate robust validation before devices can be marketed.
What Is the Difference Between Continuous Validation and Continuous Monitoring?
Continuous validation refers to maintaining assurance that a system remains validated throughout its lifecycle. Continuous monitoring is a key component of this approach, focusing on observing system performance and detecting deviations in real-time.
Validation includes additional elements such as requirements, testing, and documentation. Both concepts complement each other in sustaining compliance.
Final Thoughts
Software validation remains a cornerstone of compliance in the pharmaceutical industry, ensuring that computerized systems function reliably, safeguard data integrity, and support patient safety.
While traditional CSV frameworks continue to provide structure and regulatory alignment, the shift toward continuous software validation reflects the realities of modern digital environments. Agile development, frequent updates, and cloud adoption demand assurance models that are flexible, automated, and risk-based.
Regulators are already signaling support for this evolution through the FDA’s CSA draft, the EU Annex 11 draft, and the GAMP 5 Second Edition, all of which emphasize critical thinking and proportional validation. Companies that adapt to continuous models will not only reduce compliance risks but also accelerate system deployment and maintain inspection readiness.
The path forward is clear: validation must be dynamic, embedded, and sustained throughout the lifecycle of every GxP-relevant system. By combining strong lifecycle principles with modernized, continuous approaches, organizations can achieve both regulatory compliance and operational efficiency in an increasingly digital pharmaceutical landscape.














